|
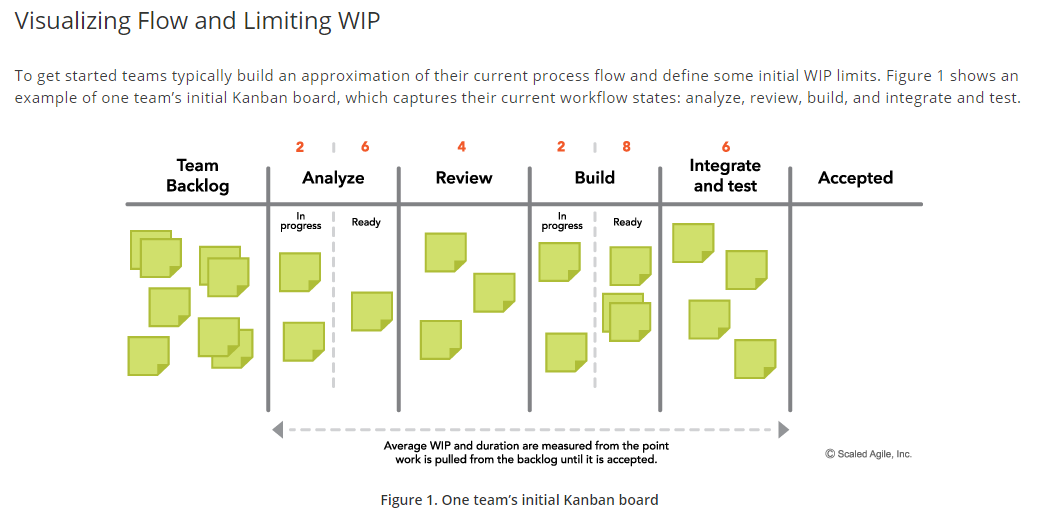
I don't often write blog posts that claim to be life-changing, but this post really is an exception. Let me start with a story about the "Wiley Old Fox"...well Dr Fox actually. So about 6 years ago I heard an incredible talk from a very eloquent and charming keynote speaker by the name....yes you guessed it.....Dr Fox. He presented at the MIcrosoft Ignite conference in Australia and he was very exceptionally entertaining. Through his elegant story-telling, he put me onto the idea that we should not check our emails first thing in the morning. Why....because it's makes us unproductive and is a counterpoint to everything agile. I can see the skeptical look in your eyes...so let me explain further. Tip of the Week: Reduce the time you spend checking your email.... So we all spend probably too much time checking out email. It's often mis-used and it can lead to hours and hours of reading and responding, that often does not lead to huge productivity gains. I set about putting together some rules, to help fix this up. These rules have stuck with me ever since. I first implemented these rules around 4 years ago when I was working as a Senior Principal Cloud Architect with DXC Technology. It was a very challenging senior position, reporting to the global CTO of an offering called MyWorkStyle. Ali Shadman was his name and he was a fantastic person to work with.....lots of fun! I had some simple rules for email engagement. My role was to lead an architecture and engineering team to deploy a private cloud in Australia. Iniitally problems were aired to me via email and it all became unmanageable, and hugely stressful. So, to avoid a burn-out situation for myself, and also to ensure that we could meet the 13 month timelines to deploy 12 brand new offerings, alll fully automated with a team of around 25-30 people.... I set about putting some new rules in place for my team and my key stakeholders: 1) Is it a complex issue and/or is it highly urgent. If YES - call my mobile. If I don't answer text me with a summary of the problem. 2) Is it a YES / NO answer to a simple question. If YES - use email. 3) Else, consider using Instant Messaging, i.e. Skype for Business, or Microsoft Teams (which didn't exist 6 years ago). This was after taking Dr Fox's advice and doing the following at the beginning of each day: 1) Read your weekly, monthly and yearly outcomes that you wish to achieve. If you haven't already, you should have these in an Outcomes Kanban. 2) Write down all the work that needs to be done for that day in a Task Kanban. If necessary schedule meetings for the next few days. 3) Then.....check your emails. If you're not sure what a Kanban is....check out this awesome article below from the Scaled Agile Framework, known as SAFe. As an instructor I ran the Leading SAFe courses for ALC Training: :
You'll find that when you think about outcomes first, and then think about your daily work, you will focus on what is important. Which should hopefuilly be the outcomes. This will then put your mind into a state where you're not being driven by emails. Now....it's quite possible there will be some urgent items in the email that require attention. Maybe your sponsor needs someething done urgently today or there is a pressing urgent technical issue that requires some attention. Simple...add 1 task to call your sponsor, and another task to call the person who is raisinig the technical issue. That's it. You don't have to spend hours bouncing emails back and forth, trying to solve just those two problems. What about the rest of your email......well if you're working with your stakeholders effectively, you will have influenced them to follow the first set of rules. Influencing people in a positive way, is probably another blog post....or two. It took me a few months, but eventually my emails were down to maybe 5 or 6 a day, that were simply YES/NO questions. All email that I was cc'd in, went into folder. I also encouraged people not to CC me in stuff, as it wasn't ever going to help. Some people think, but that may be useful one day....well if an issue comes up....there are better ways of resolving....than to point to your past emails and said "I told you so". That doesn't build positive relationships and doesn't help with solution deployment, so why do it. Feel free to continue the conversation on: Twitter: https://twitter.com/musiccomposer1 LinkedIn: https://www.linkedin.com/in/paulcolmer/ Instagram: https://www.instagram.com/paulcolmer/?hl=en Have an awesome day beautiful people. 😎❤
0 Comments
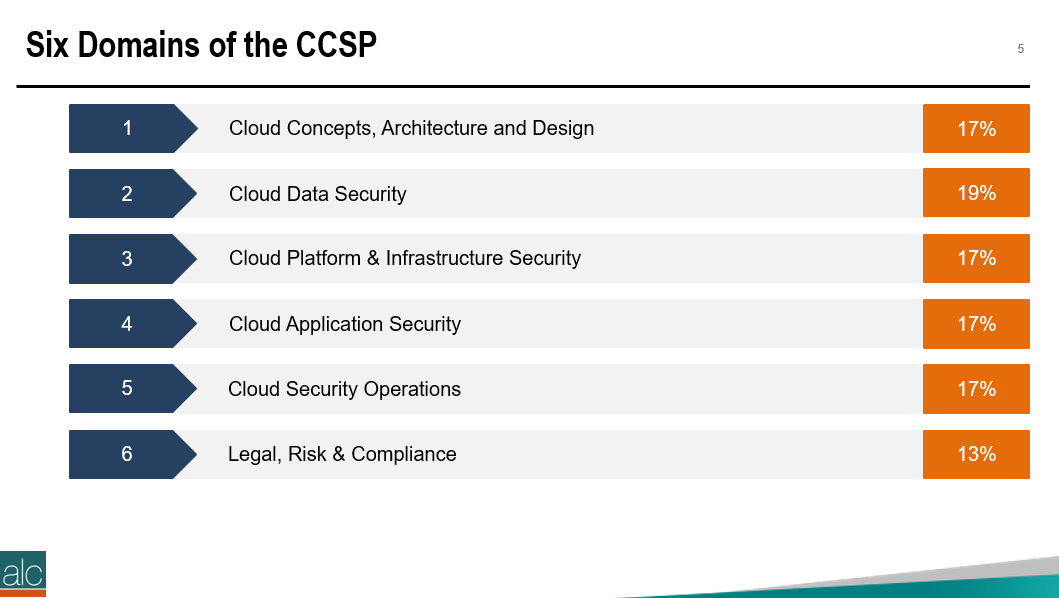
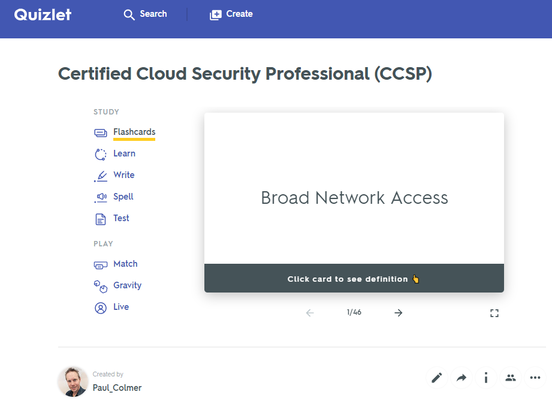
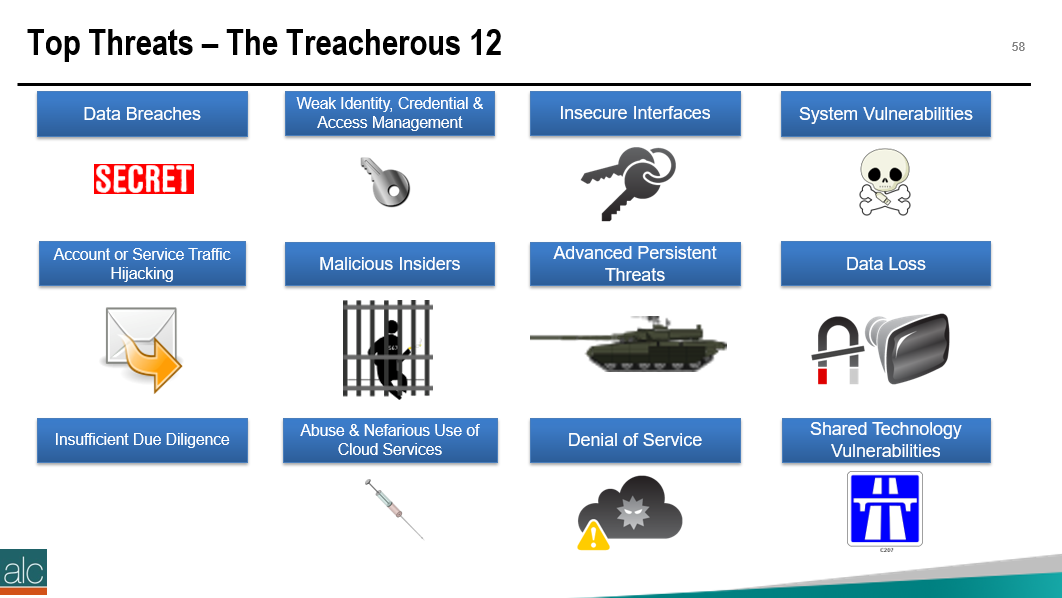
The Certified Cloud Security Professional certification is offered by the ISC2 and is one of the many courses I have helped develop at ALC Training. It is proving to be one of the most popular certifications that I run....I have 11 others that cover cloud computing, agile, cybersecurity and big data areas. But why? As you can see, it covers 6 domains and we focus on a range of techniques and best practices associated with cloud computing. For those studying CCSP, I have created a free flashcard quiz below. This is handy for anyone that is involed in CyberSecurity and is a good way to re-enforce your knowledge. For a detailed list of learning outcomes check out the ISC2 website below.... The reason I think CCSP is popular, is because CyberSecurity is in the Top 5 items that keep senior leaders awake at night. The fear that the organisation you have worked hard to protect, could one day be maliciously attacked is a troubling thought for many...resulting in a cold sweat nightmare at 3am in the morning. To be honest there are many things that business leaders need to consider. So let me outline 2 of the key items that spring to mind this morning.... 1 - Secure the use of Identity and Access Management Systems The key here is people....because they are the solution....not the problem. Here is a simple checklist that everyone can follow...not just at work...but also at home. Tip 05 can be adapted for business, by building a list of trusted sources, i.e. a whitelist. You can do this manually, or by using a whitelisting tool, preferably one based on Artificial Intelligence technology. That way it can detect not just trustued sources that you list, but predict or warn when something looks malicious. 2 - Simulate Probable Security Scenarios Again the key here is people. Create a realistic scenario....data breaches are the most common, so this is a good place to start. Brief a small number of individuals, including leadership, that you're creating a simulated security challenge....execute the scenario for real on a non-production system with the team....then treat it like a fire drill and allow the remainder of the team to see how they react and recover from the simulation. It's a bit like paintballing...where one team attacks the castle....and the other team defends it. Although in this scenario....the defending team is really ascertaining what happened and how best to protect the organisation going forward. If you need inspiration for what threats you should be simulating....take a look at the Treacherous 12....which we cover in the CCSP course. Have a secure and safe day beautiful people. ❤😎🚀
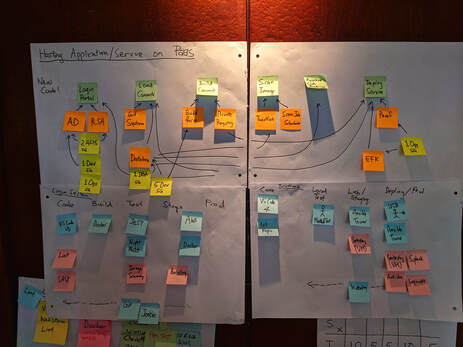
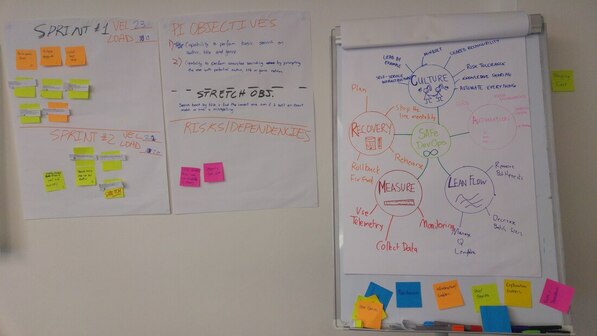
8/6/2019 0 Comments How to Be Agile?I've been running some DevOps, Agile and Cloud Computing courses the past 2 weeks. A common question that I'm asked...is what exactly is Agile and what does it mean to be Agile. Simply put...Agile is a mindset...where you're able to take a problem....divide it up into very small pieces...and execute as efficiently as possible using lean flow techniques....agile principles....feedback loops....whilst allowing yourself to experiment, fail and learn to produce a significantly better outcome. Lean flow is all about eradicating waste....things like shorten waiting times....don't pass defects or problems downstream to the next person....relying less on email and more on face to face communications....as well as experimenting with smaller targeted meetings of 30 minutes or less. Value stream mapping is a very effective tool for understanding the flow of work between teams.....as illustrated by my fantastics students below: Agile principles include.....decentralised decision-making by allowing others to experiment, fail and learn, whilst creating a safe enviromment...free from blame and finger pointing. Not jumping into solution-mode...instead preserving options....until much later in the solution lifecycle...thinking of functions and capabilities, rather than tech. And finally unlocking the intrinsic motiviations of knowledge workers....simply put...give your people Autonomy, Mastery and Purpose. Below is some artifacts from a PI Planning simulation that I run on our Leading SAFe course. It's all part of the Scaled Agile Framework which includes the above Agile principles: Finally feedback loops....by asking your client how you can improve...asking your stakeholders their key concerns....automating your tasks....especially tests....and ensuring all your work is visible...especially with a large geographically dispersed team. Using physical and digital Kanbans are great methods for reminding the team what needs to be done...and also helps to celebrate the wins...especially the small ones. Students in my cloud security (CCSP) class are using the Kanban technique to derive work that covers some of the top cloud security threats: What does Agile mean to you?
|
CategoriesAll Active Directory AI Architecture Big Data Blockchain Cloud Comedy Cyber DevOps Driverless Cars MicroServices Office 365 Scaled Agile Social Media AuthorPaul Colmer is an AWS Senior Technical Trainer. Paul has an infectious passion for inspring others to learn and to applying disruptive thinking in an engaging and positive way. Archives
May 2023
|










 RSS Feed
RSS Feed