|
I hope everyone is staying safe and making the most of their time indoors. Today I am rediscovering the beauty and elegance of Amazon Web Services or AWS for short. AWS provide a cloud computing platform that allows you to build apps and infrastructure to deliver business outcomes. Today, my session is going to focus on a very basic service called Elastic Compute Cloud or EC2 for short. It is a simple service that allows you to build your own virtual machines or VMs. These VMs are the most basic building block in cloud computing. Below is a fantastic Zoom video, that steps you through some of the basics of AWS EC2 and provides you with a simple hands-on demo on the AWS platform. I really hope you enjoy it.
0 Comments
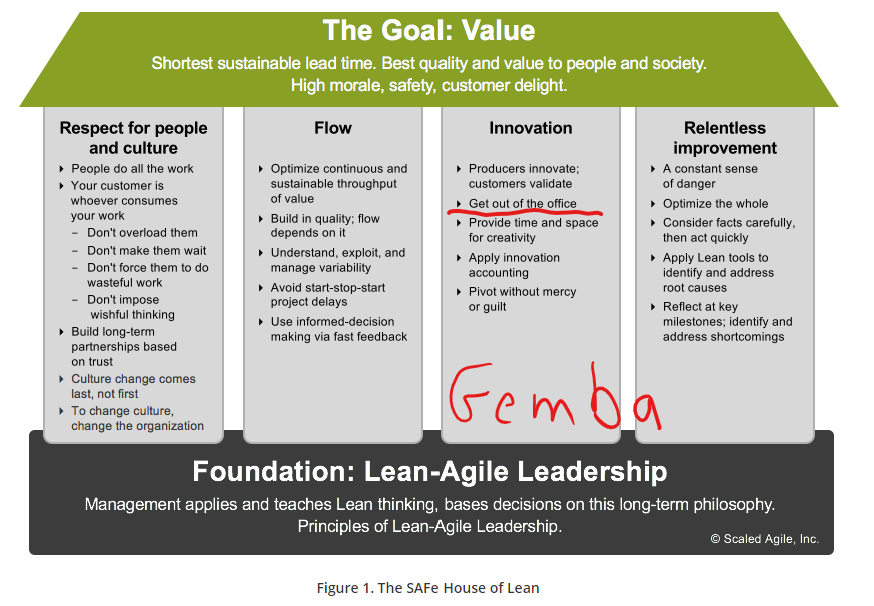
"Hi everybody....as always I hope you're doing fantastic"....is a great opening for a brilliant new YouTube channel, that I recently discovered called Mentour Pilot. I love this channel, because you get to learn lots about real flying, planes and pilots, and the presenter is an active pilot himself. Check him out by clikcking the image below. Isn't the doggy cute....😂 But what has that got to with comedy......it's another source of learning.....just like comedy. Yesterday.....I performed my 10th standup routine last night in Brisbane to a phenomenal crowd and felt really comfortable delivering my 6 minute set. Why did I start this comedy journey.....to grow....to learn and above all....have fun. When it stops being fun.....I'll switch to something less boring instead. Click on the image to see my latest Instragram pics...so I can share all the fun with all or you....😍 Everytime I stand on that stage....I pick up maybe 5-10 learnings every time. Things such as making eye contact with everyone in the crowd...using tone and accent to vary the delivery....walking confidently up to the stage and making sure I have a strong grasp of the mic....but last night I'd like to share 3 very personal learnings....that you can all take with you into everyday lives. 1 - Sit with the Crowd and Enjoy all the other acts (Gemba)In Agile, we call this Gemba....which literally means the "place where work is done". In a manufacturing plant, it is the factory floor, in a hospital it is the wards and theatres, in a retail supermarket, it is the stock rooms and supermarket aisles....it's where the front-line workers experience the good and bad in a business. In comedy it's sitting with the audience. Why is this important? 🤔 In comedy, you can tune into your audience....gauge their reactions to the other comedians and learn fast....so that you provide an entertaining set for your audience. You can feed off the jokes of others and see how people are reacting....it gives you a chance to tune-in and learn. Below is a diagram from one of my Scaled Agile Framework courses...I've underlined the need to "get out of the office"....or "get out of the ivory tower" which is what Gemba is all about....click on the link to view our 2 day Leading SAFE course: 2 - Prepare a Detailed ScriptAlways go into a comedy routine with plenty of preparation. It might look like a casual conversation with the audience....but that's all part of the act and the art. Great comedians leave nothing to chance, outlining every nuance, every gesture, learning every word....until their script is memorised word and action perfect. I call this my foundation. It's like a house....I can now build on this on. 🏠 From here, I now have the confidence to line-up an opening joke using a reference from a previous comedian, or something I saw today on tv, or maybe even the weather. In other words, I can now improvise or try out new material. This worked very well in New York, being the token Aussie....and Melbourne....being the token Queenslander from a hot state. You can check out my New York set on YouTube here: 3 - The 60 Seconds before you walk onto the stage is the most criticalSoaking up the audience atmoshpere and then distilling that into 60 seconds is critical. I need to remember...I'm here to entertain the audience....not make them laugh. The best advice I ever received was 'NEVER....EVER....try to be funny". Sound counter-intuitive, but I'm not a professional comedian. Why would I put myself under that pressure. So I go out there to entertain. The laughs are a bonus. The more I focus on the crowd...the more laughs I get.
Also....people come to enjoy themselves, to have fun and escape for an hour or so. Let me help them with that journey. Let's escape together...for 6 minutes...in a unique world....the world of The Digital Coach...where fact is funnier than fiction. 🚀 I hope you enjoyed this blog post. Feel free to reach out social media and provide your feedback. It's very much appreciated. 😎 LinkedIn 👨🏫 www.linkedin.com/in/paulcolmer/ Twitter 🌍 twitter.com/musiccomposer1 Instagram 🐯 www.instagram.com/paulcolmer/?hl=en Have an awesome week beautiful people.... P In this blog article, I'm going to outline the key steps required to help transform a medium to large organisation. Digital Transformation is the ability of an organisation to change their culture, in order remain competitive. By using new technologies more effectively than their competitors, this leads to greater market share, lower price points, improved product and/or service quality and constant innovation for clients. Notice that I start with culture, not technology. I'll draw on my 20+ years of hands-on experience as a solution architect and professional technologist with DXC Technology and Santander, as well as my expertise in running cultural change and technical courses at ALC Training & Consulting. Here are the key steps and they are in order:
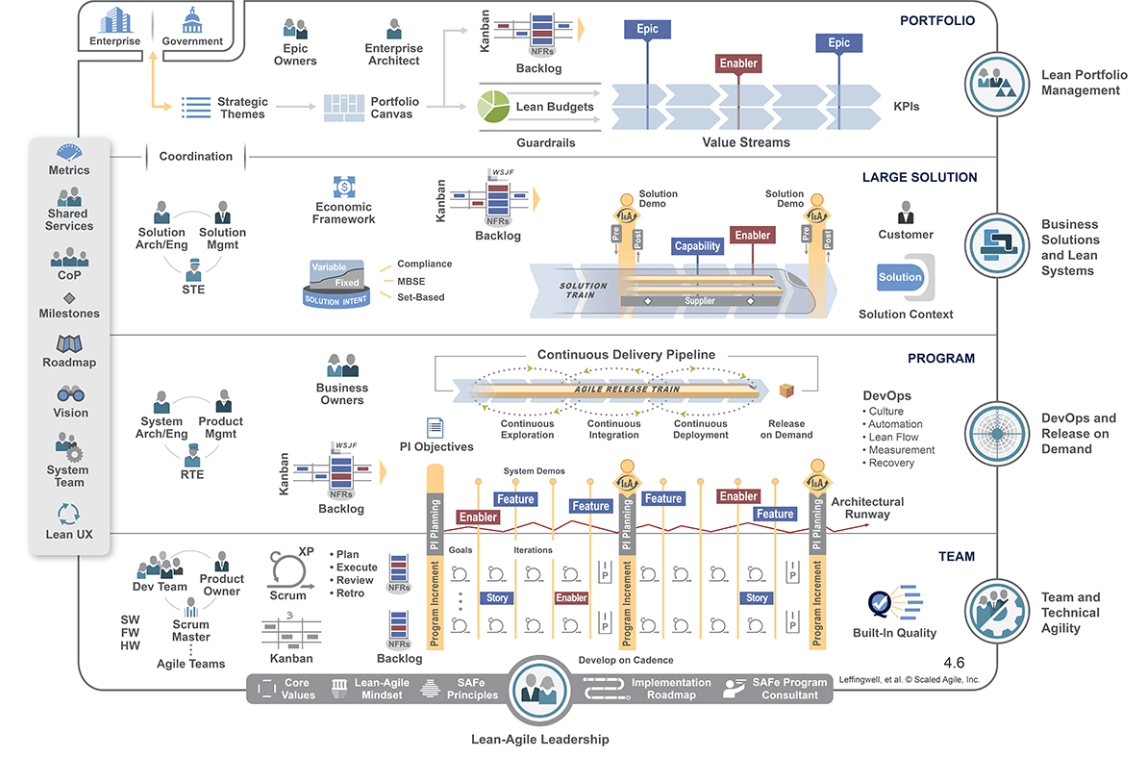
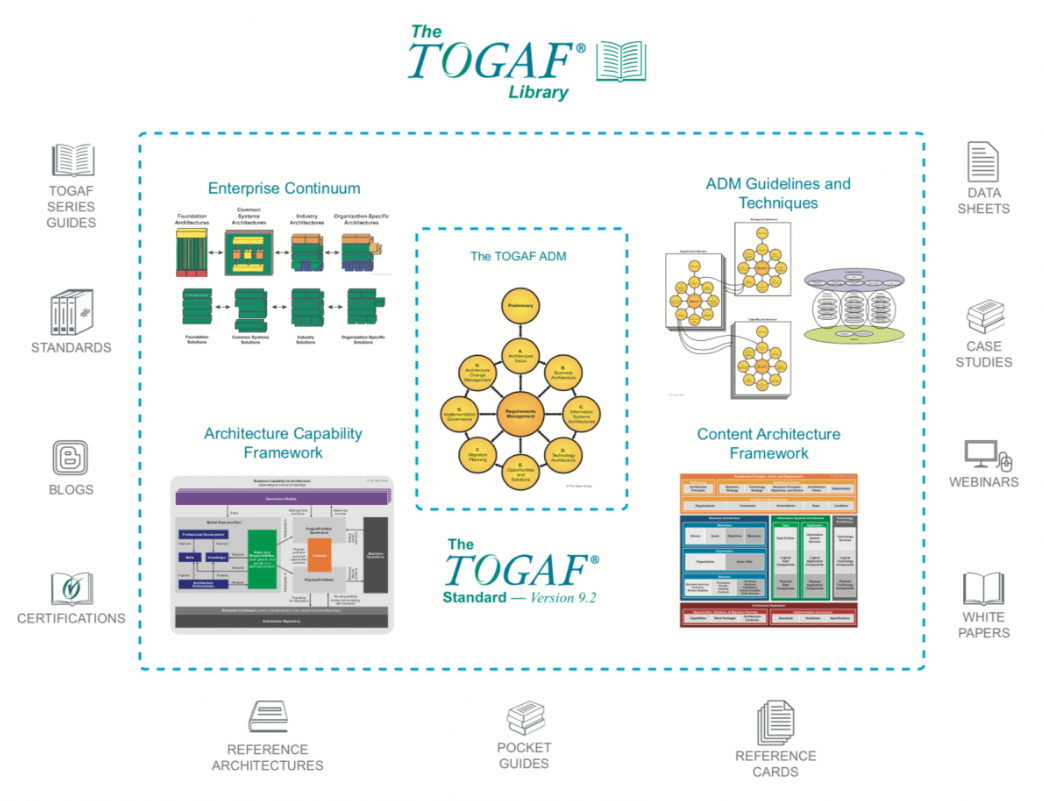
This is the Scaled Agile Framework (SAFe): And this is the top slice of TOGAF. You would use TOGAF as part of the architecture functions in SAFe.
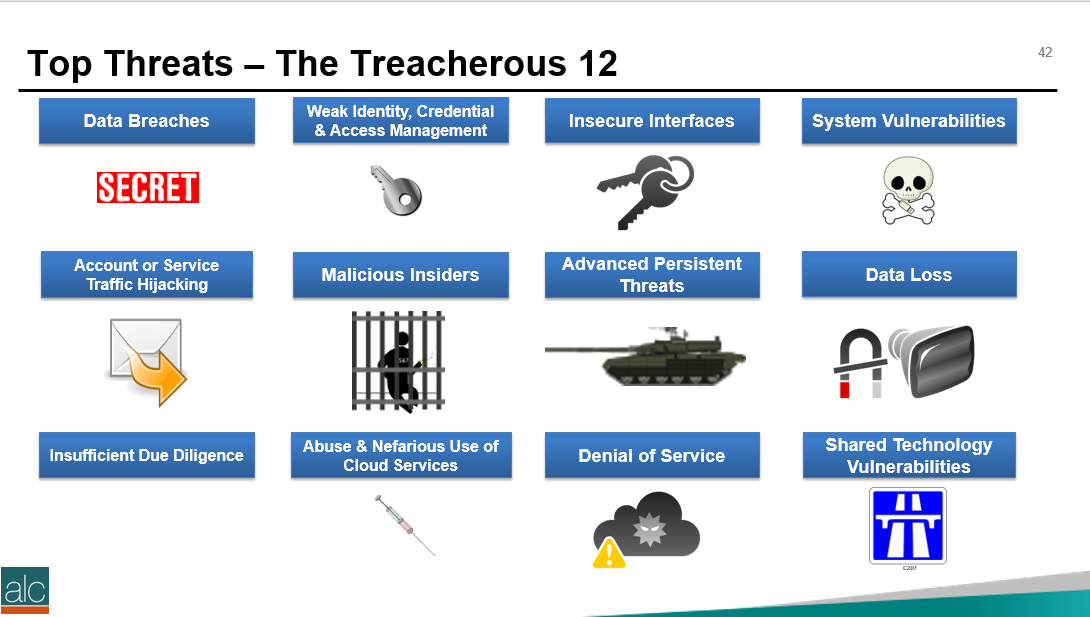
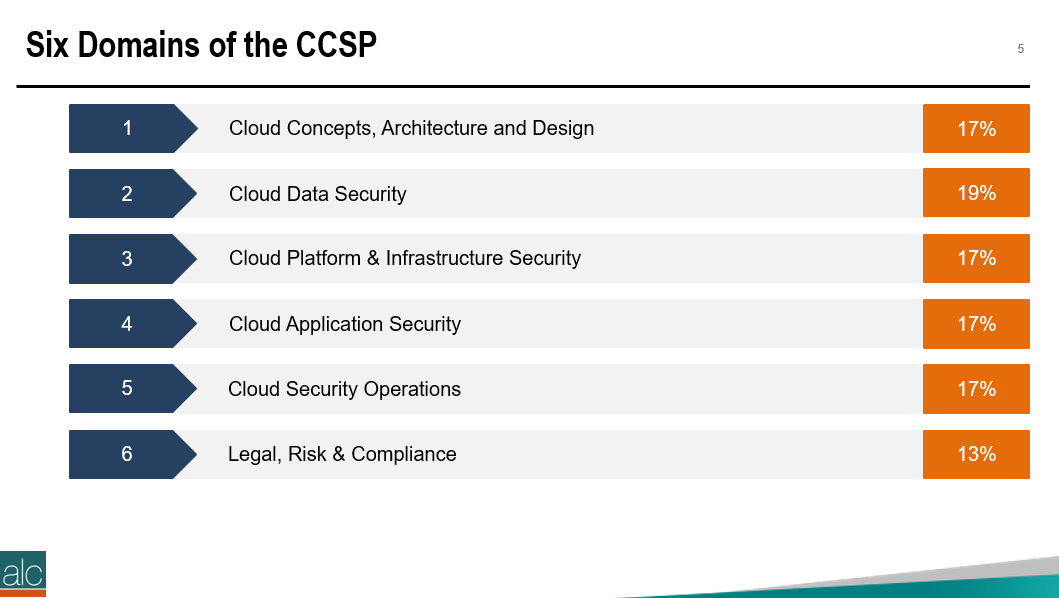
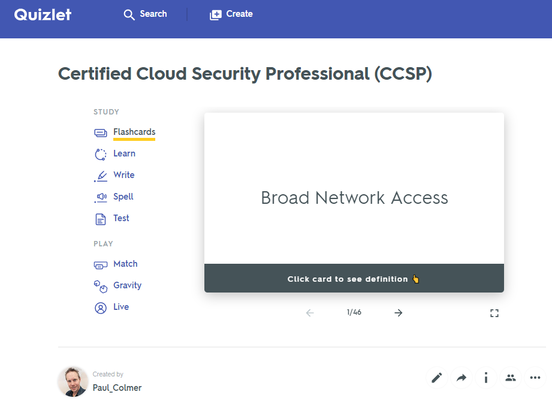
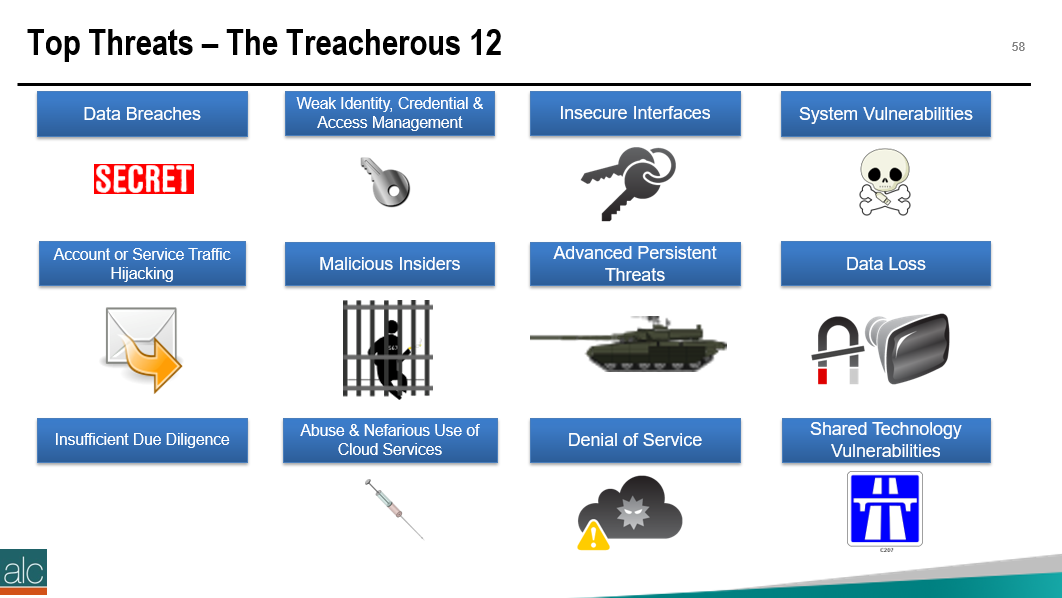
Do you have questions with these steps? Feel free to reach out to me directly: Twitter: twitter.com/musiccomposer1 LinkedIn: www.linkedin.com/in/paulcolmer/ Instagram: www.instagram.com/paulcolmer/ Have an awesome week, beautiful people. The Certified Cloud Security Professional certification is offered by the ISC2 and is one of the many courses I have helped develop at ALC Training. It is proving to be one of the most popular certifications that I run....I have 11 others that cover cloud computing, agile, cybersecurity and big data areas. But why? As you can see, it covers 6 domains and we focus on a range of techniques and best practices associated with cloud computing. For those studying CCSP, I have created a free flashcard quiz below. This is handy for anyone that is involed in CyberSecurity and is a good way to re-enforce your knowledge. For a detailed list of learning outcomes check out the ISC2 website below.... The reason I think CCSP is popular, is because CyberSecurity is in the Top 5 items that keep senior leaders awake at night. The fear that the organisation you have worked hard to protect, could one day be maliciously attacked is a troubling thought for many...resulting in a cold sweat nightmare at 3am in the morning. To be honest there are many things that business leaders need to consider. So let me outline 2 of the key items that spring to mind this morning.... 1 - Secure the use of Identity and Access Management Systems The key here is people....because they are the solution....not the problem. Here is a simple checklist that everyone can follow...not just at work...but also at home. Tip 05 can be adapted for business, by building a list of trusted sources, i.e. a whitelist. You can do this manually, or by using a whitelisting tool, preferably one based on Artificial Intelligence technology. That way it can detect not just trustued sources that you list, but predict or warn when something looks malicious. 2 - Simulate Probable Security Scenarios Again the key here is people. Create a realistic scenario....data breaches are the most common, so this is a good place to start. Brief a small number of individuals, including leadership, that you're creating a simulated security challenge....execute the scenario for real on a non-production system with the team....then treat it like a fire drill and allow the remainder of the team to see how they react and recover from the simulation. It's a bit like paintballing...where one team attacks the castle....and the other team defends it. Although in this scenario....the defending team is really ascertaining what happened and how best to protect the organisation going forward. If you need inspiration for what threats you should be simulating....take a look at the Treacherous 12....which we cover in the CCSP course. Have a secure and safe day beautiful people. ❤😎🚀
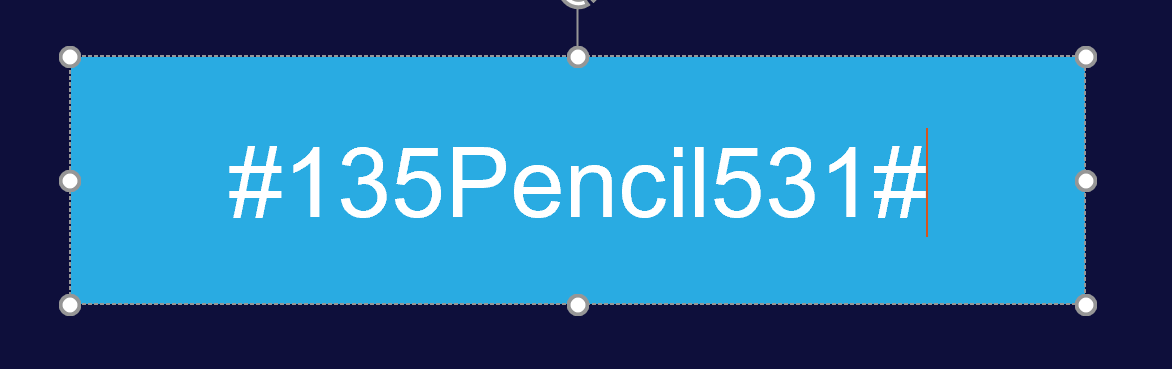
This blog article is designed to be ready by everyone. By everyone, I mean people who are new to the cloud, and maybe uploading a picture of their great grand children to Facebook, for the first time. Or maybe you're a seasoned technologist, like myself, with over 300 cloud-based logins. Chances are, you're probably somewhere in the middle, and this is perfect for you too. The 5 simple tips I have outlined above, will help everyone. They're universal to everyone that uses the cloud. They are simple to implement, and need you to put aside a little time. They will protect you from cyber attacks. Oh...and I also follow these 5 tips myself. Probably for about the past 5 years. I will not only explain how to implement each tip, but I will give you a specific personal examples. That way, you know my advice is real and that I follow my own advice. Only a fake person wouldn't follow their own security advice....right.....? Each image in this blog is clickable, offering additional information about that subject. What is a Complex Password?Let me show you what a complex password looks like: If you click on the image, it will take you to Troy Hunt's blog on passwords and hacking, which explains a bit more around why complex passowrds are important. Let me break this down for you.
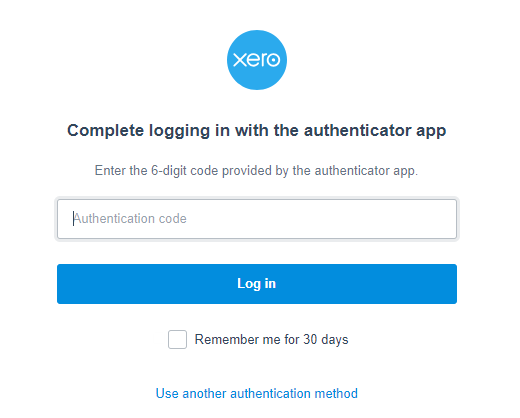
What is Multi-Factor Authentication?It's a service, that most well-known cloud providers, now offer, as a means of additional security protection. Let me break it down with a specific example. I'm going to outline the overall approach using a cloud app called Xero. It is used for accounting and I love it: Using Xero as an example, here is how it works, once it is configured:
If you're not sure, whether you cloud service offers MFA, either contact them directly, or perform a Google search to look up whether they offer the service. You may need someone technical to help setup for you, or if you have paid support, you call up your cloud provider. You can also reach out to me publicly on twitter: @MusicComposer1 I'm always willing to help 'coach' you through to success. What is a Password Manager?t's an app that you download that stores all your passwords for you. It's very, very important that you create a complex password to open the app, as this becomes your key to all your other passwords. You also want to setup multi-factor authentication. Typically the average technical person probably has around 200-500 cloud accounts they use or have used. So for the average person, 50-100 cloud accounts is not unusual. If you're using an app on your mobile phone, then you most likely have a username and password for that app. Therefore if you have 100 Apps on your phone, you will probably have close to 100 usernames and passwords. Clearly it's very difficult to remember 100 different passwords, so the password manager really comes into play here for everyone. There are also two extra benefits, among many, that password managers provide:
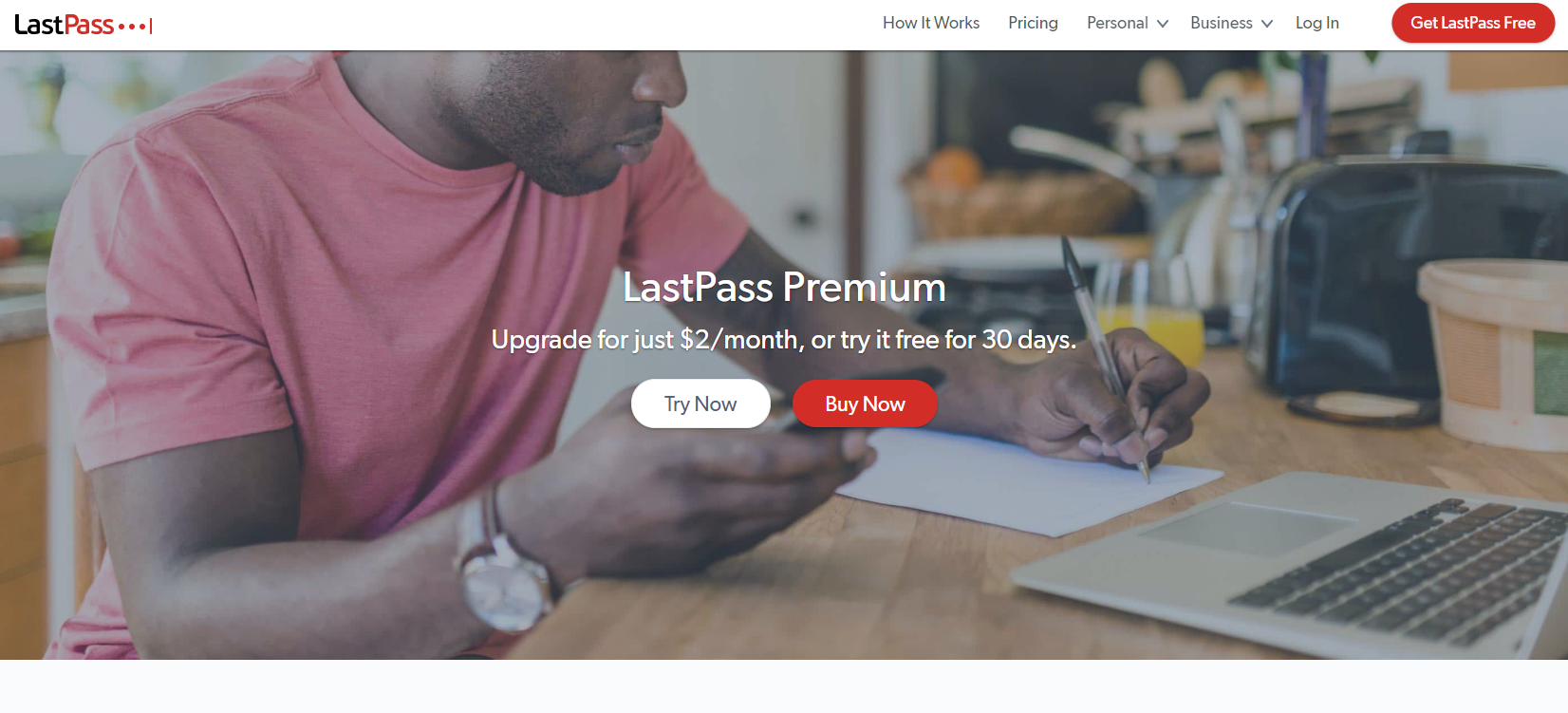
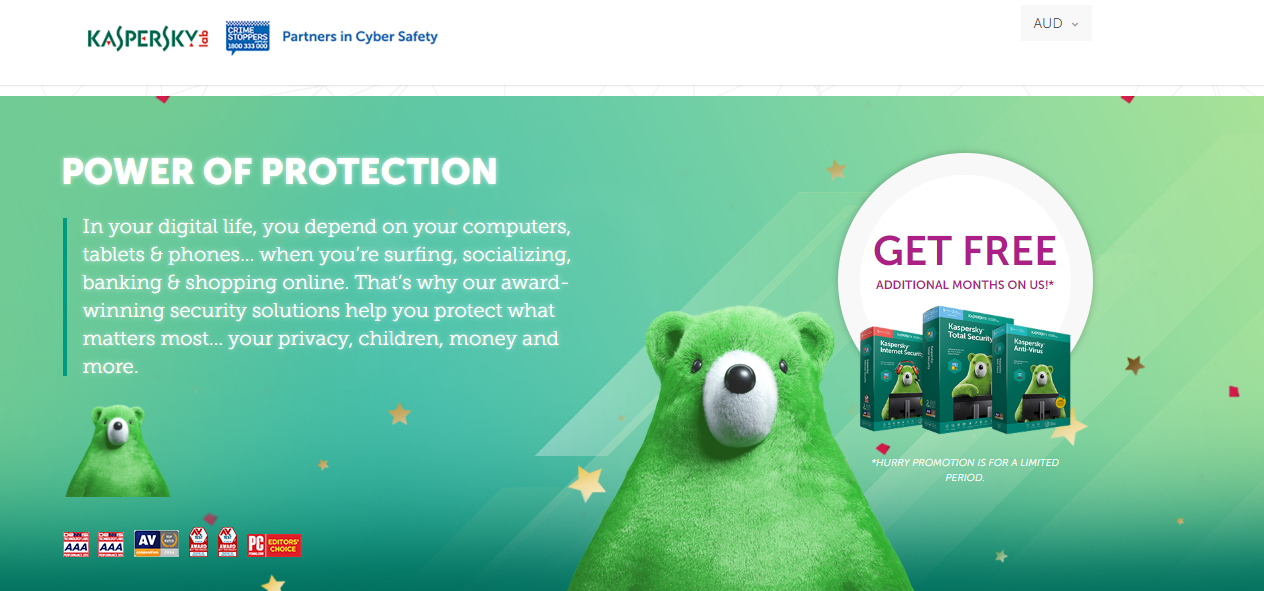
When changing your password, I would recommend doing this every 12-24 months, for all your accounts. And also delete cloud accounts that you no longer use. WHY? Because that cloud provider may suffer a data breach in the future. A data breach is where a hacker gains data from a cloud provide. This could mean a malicious actor, could use your account to attempt to steal your money, damage your reputation or worse still assume your identity. My top pick is Last Pass and I would recommend the Premium (Paid) version: What is Anti-Malware Software? This is an app that helps detect any malicious activity on your device. Sometimes known as anti-virus software, however devices can be attacked not just via virus, but also via many other attack vectors. So I prefer the term anti-malware. I personally install anti-malware software on my Android phone and my Windows 10 machine. I don't install it on my Mac or my iPad. However, I would recommend that you install it on all your devices. Generally when you buy anti-malware software they give you a number of licences to run on different types of device, so it probably won't cost you extra. So I always recommend this extra level of protection. The reason I don't do that, is because I have additional security controls to mitigate this risk. These are a little complex to explain. I also don't want to give away this information to potential hackers, who could also exploit me personally. I hope that makes sense. :-) My top pick here is to use the Kaspersky. I've personally used it for probably 10 years now. I came across it, when I was running high-powered flight simulation sofwtare on my machine and I wanted anti-malware software that would detect incoming threats, as well as viruses, without sucking all the processing power from my computer. I found that Kaspersky was the most cost effective and smallest footprint softoware on the market at the time, and have used it ever since. What is SpearPhising or Phising?Never click on links in an email, that are sent from outside your company. WHY? Because you are opening yourself up to a Spearphising attack. Sometimes also known as a Phising attack for short. So a Phising attack, is when a malicious actor, sends you an email with a link inside. You click on the link and a number of bad things can happen:
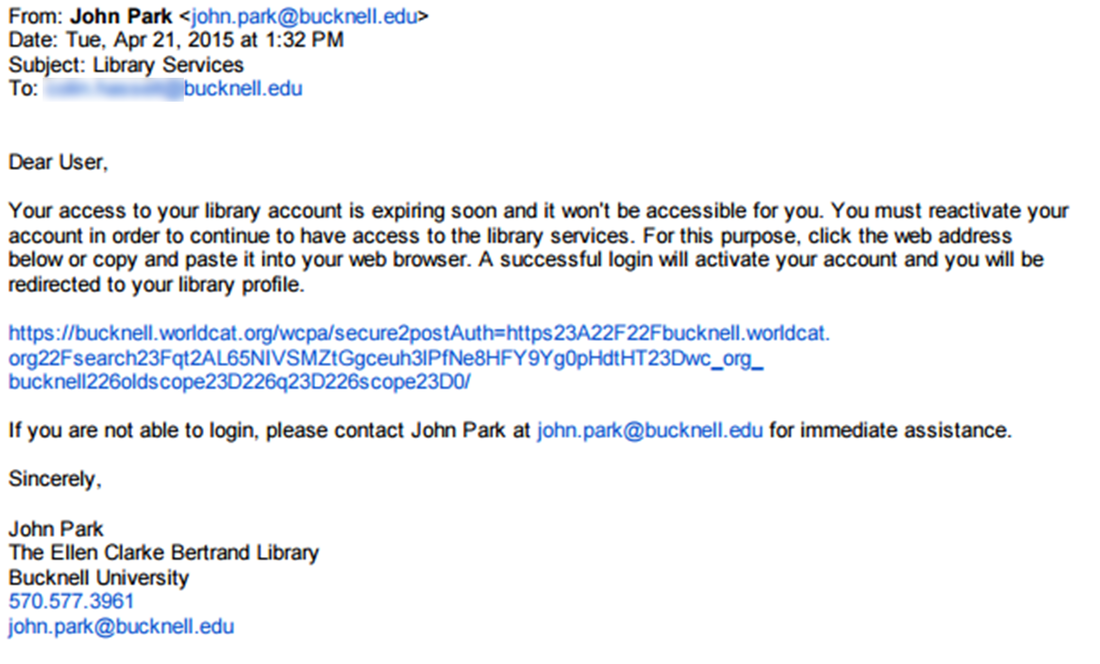
Here is an example, of a reasonably sophicated phising attack: Click on the link above to be redirected to another simple definition of Phising.
But what about if you do business with external companies? That's fine, we can modify this advice. Make a note of all the people you personally deal with outside your company. Agree with them, using the phone, how you're going to communicate via email and how you're going to share information. I personally use the OneDrive cloud links to share read-only files and I always set the link to expire after 30 days. By creating a list, you're effectively creating a 'whitelist'. A list of people whom you trust. There is no guarantee, that someone else won't impersonate them, so by having an agreed format for the exchange, you can validate if it is genuinely from that person. If in doubt, give them a telephone call. You know that old-fashioned thing, that emails has replaced.......LOL. If you're dealing with clients directly via email, then you'll hopefully be validating them as leads anyway, so there shouldn't be any reason to click on the links they are sending you. If you're business is truly an exception to this rule, and clients need to send you a link then you're need additional security:
And remember...be aware but not alarmed. Cybercrime is relatively rare. Follow these tips and you'll put yourself in the Top 10% of the population, which means you're highly unlikely to be scammed. Below is a great website to check for the latest scams too: |
CategoriesAll Active Directory AI Architecture Big Data Blockchain Cloud Comedy Cyber DevOps Driverless Cars MicroServices Office 365 Scaled Agile Social Media AuthorPaul Colmer is an AWS Senior Technical Trainer. Paul has an infectious passion for inspring others to learn and to applying disruptive thinking in an engaging and positive way. Archives
May 2023
|

















 RSS Feed
RSS Feed