|
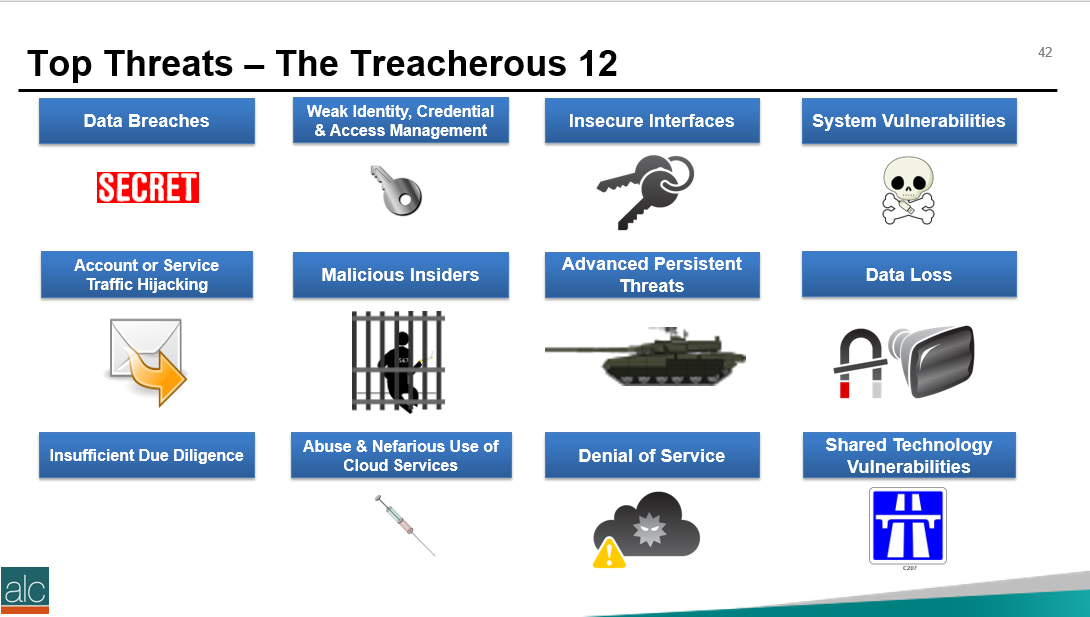
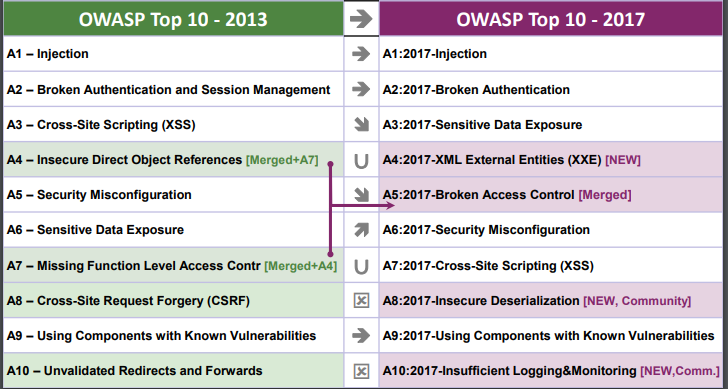
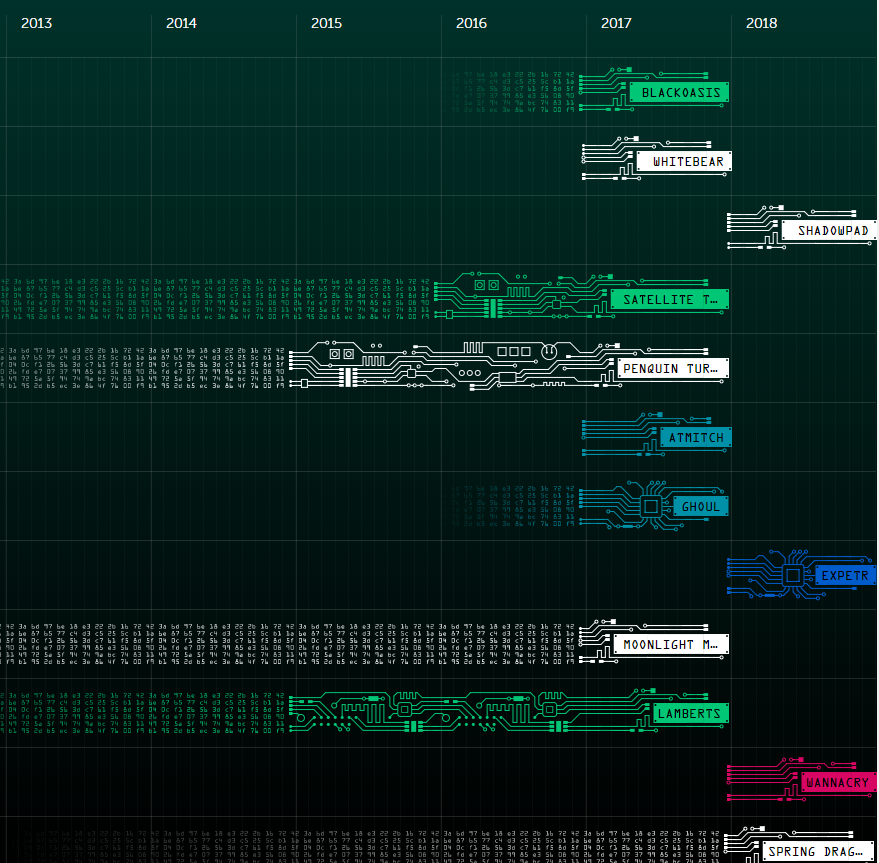
Today is my first day back as a cloud cyber coach in 2018. So I thought I'd start off the year with a quick revision of the Cloud Security Alliance Top #Cloud Threats, known as the Treacherous 12. This was updated to include specific real-life examples in November 2017: https://downloads.cloudsecurityalliance.org/assets/research/top-threats/Treacherous-12_Cloud-Computing_Top-Threats.pdf Followed by more revision of the OWASP Top 10 threats that are relevant when developing software, which was updated in 2017: https://www.owasp.org/images/7/72/OWASP_Top_10-2017_%28en%29.pdf.pdf This lead to me to refresh my memory on the most significant advanced persistent threat (APT) events of 2017, as well as the definition of an APT. So an Advanced Persistent Threat is a specialised and generally sophisticated attack that we often associate with CyberWarfare and Cyber espionage. It generally consists of installing malicious software onto a number of hosts into an organisation, orchestrated by a third party, and results in some form of damage to the infected organisation, i.e. credit card data being exposed (Sony) or data being destroyed via encryption (WannaCry). A found a great resource from Kaspersky Labs that provides a visual dashboard for all known APTs. https://apt.securelist.com/#!/threats/ Here are the Top 3 most dangerous threats found towards the end of 2017:
1 ShadowPad - A company called NetSarang produce server management tools for large corporate networks. Their products, available via download, had become infected with an encrypted payload from a malicious actor. Software should be removed and the latest 'clean' copies installed. https://securelist.com/shadowpad-in-corporate-networks/81432/ 2 NoPetya / ExPetr - This is ransonware which is spread via the use of custom tools, such as Mimikatz. It reboots the system after infection and starts to encrypt data onto NTFS partitions, which affects Windows PC's and servers. https://securelist.com/schroedingers-petya/78870/ 3 WannaCry - Well publicised in the media, this is also ransonware, and exploits a known vulnerability on Windows devices, called 'EternalBlue' . If your Windows devices are patched against EternalBlue exploit, then you're safe, however many organisation did not and were susceptible to WannaCry. https://securelist.com/wannacry-ransomware-used-in-widespread-attacks-all-over-the-world/78351/ https://twitter.com/DigitalColmer
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
CategoriesAll Active Directory AI Architecture Big Data Blockchain Cloud Comedy Cyber DevOps Driverless Cars MicroServices Office 365 Scaled Agile Social Media AuthorPaul Colmer is an AWS Senior Technical Trainer. Paul has an infectious passion for inspring others to learn and to applying disruptive thinking in an engaging and positive way. Archives
May 2023
|


 RSS Feed
RSS Feed