|
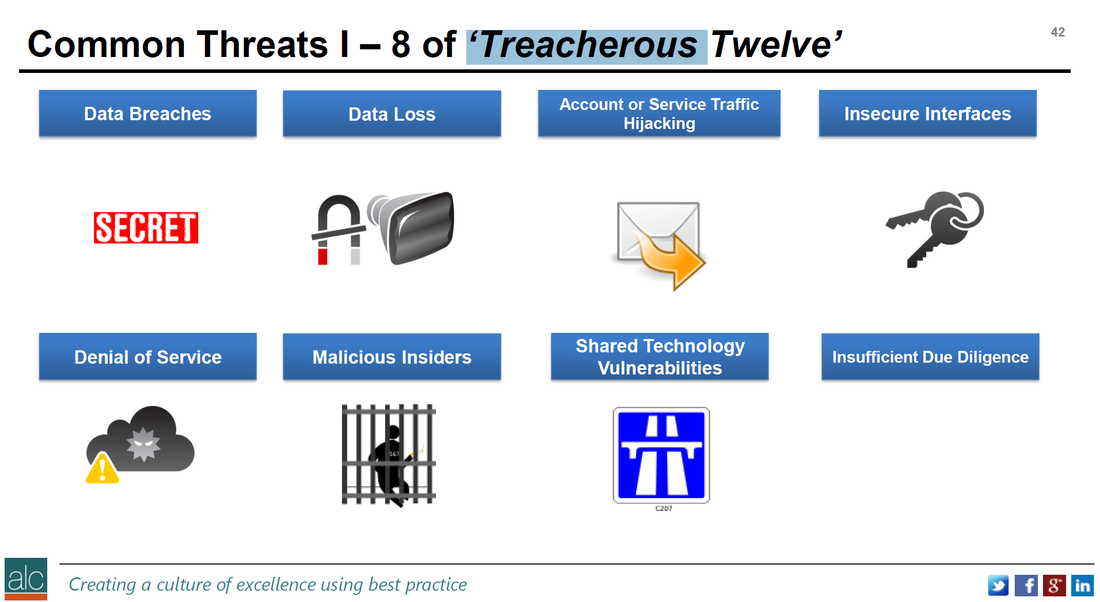
As part of our Certified Cloud Security Professional #CCSP, we go into some detail around what is known in the security industry as the 'Treacherous Twelve.' These are the Cloud Computing Top Threats that were prevalent in 2016 based on data and input from various sources and contributors and co-ordinated by the Cloud Security Alliance and culminates in an easy to read and consume report. This report can be downloaded here: https://downloads.cloudsecurityalliance.org/assets/research/top-threats/Treacherous-12_Cloud-Computing_Top-Threats.pdf The diagram below shows the first eight threats: The report focuses on 12 threats that are specific and real in cloud computing solutions and as of the 20th October was updated to include real-life examples of each threat. The report is particularly useful in outlining clear business scenarios, where these types of threats are going to keep the board of directors, awake at night.
Business scenarios could include the hacking of a public-facing website, leading to reputational loss or severe damaging of a brand with years of investment, or the realisation that an ex-employee that has now signed-up with a competitor, is leaking your intellectual property which took several months to build up. Here is an executive summary of the first 5 threats out of the twelve: Data Breach - an incident where sensitive, protected or confidential information is released, viewed, stolen by an unauthorised actor. In 2015, BitDefender users names and passwords were stolen from an AWS hosted system and a ransom of $15,000 demanded. Weak Identity, Credential & Access Management - often leading to data breaches as a result of inefficient or ineffective identity access management systems or processes, such as the use of weak passwords, bypassing multi-factor authentication or improper rotation of cryptographic entities, such as keys, passwords or certifications. Praetorian, a US-based provider of security solutions, launches a solution that cracks password hashes in a simple fashion, using AWS services. Insecure API's - failure to provide appropriate security controls around application programming interfaces. In 2015, the US Internal Revenue Service (IRS) exposed over 300,000 records via an insecure Get Transcript API call. System and Application Vulnerabilities - defects in software that allow hackers to steal data, take control of a system or disrupting services. WannaCry made use of an unpatched defect in Microsoft Windows operating systems, particularly Windows XP and allowed the malicious actors to encrypt data in an attempt to extort a ransom. Account Hijacking - the ability for hackers to seize usernames and passwords to hijack an account, usually gained through phishing, fraud of exploitation of software vulnerabilities. Here are 7 other reasons to read the report:
Paul Colmer is the lead digital architect ALC Training and Consulting. He is responsible for creating and running all the cloud security courses, which include CCSP, AWS, Azure, Office 365 and cloud foundation certifications. For more information visit: https://www.alctraining.com.au/courses/cloud-computing/ Or engage with Paul on his crazy adventures on twitter: @musiccomposer1 using the hashtag #CCSP
0 Comments
|
CategoriesAll Active Directory AI Architecture Big Data Blockchain Cloud Comedy Cyber DevOps Driverless Cars MicroServices Office 365 Scaled Agile Social Media AuthorPaul Colmer is an AWS Senior Technical Trainer. Paul has an infectious passion for inspring others to learn and to applying disruptive thinking in an engaging and positive way. Archives
May 2023
|


 RSS Feed
RSS Feed