|
In this blog article, I'm going to outline the key steps required to help transform a medium to large organisation. Digital Transformation is the ability of an organisation to change their culture, in order remain competitive. By using new technologies more effectively than their competitors, this leads to greater market share, lower price points, improved product and/or service quality and constant innovation for clients. Notice that I start with culture, not technology. I'll draw on my 20+ years of hands-on experience as a solution architect and professional technologist with DXC Technology and Santander, as well as my expertise in running cultural change and technical courses at ALC Training & Consulting. Here are the key steps and they are in order:
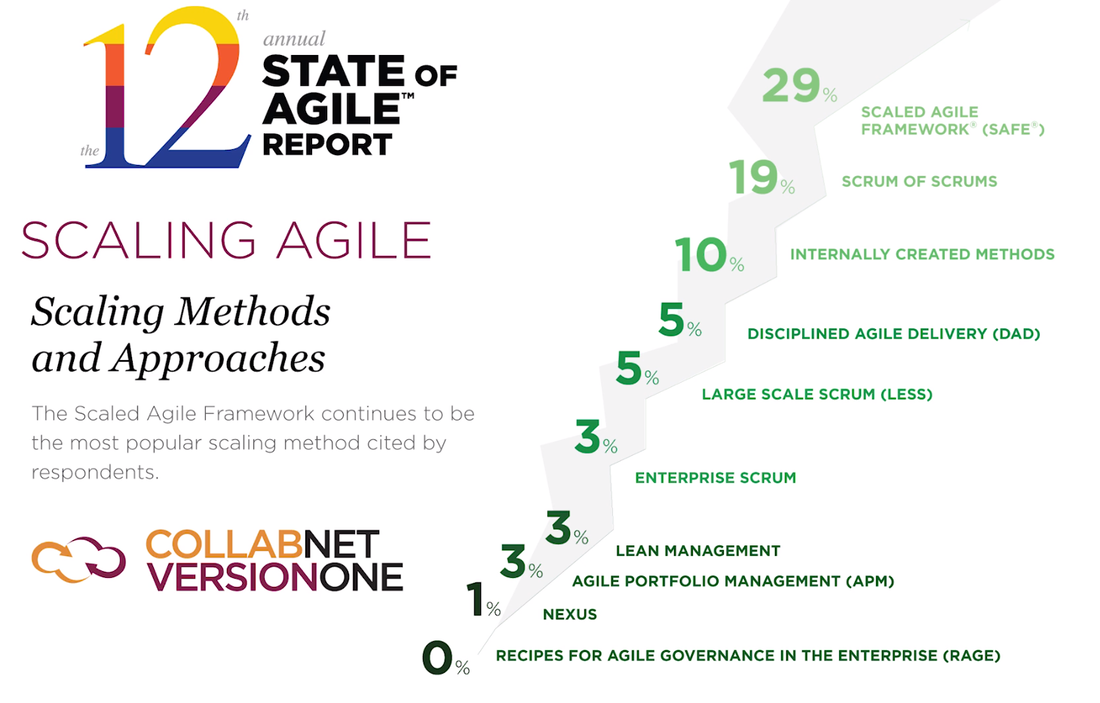
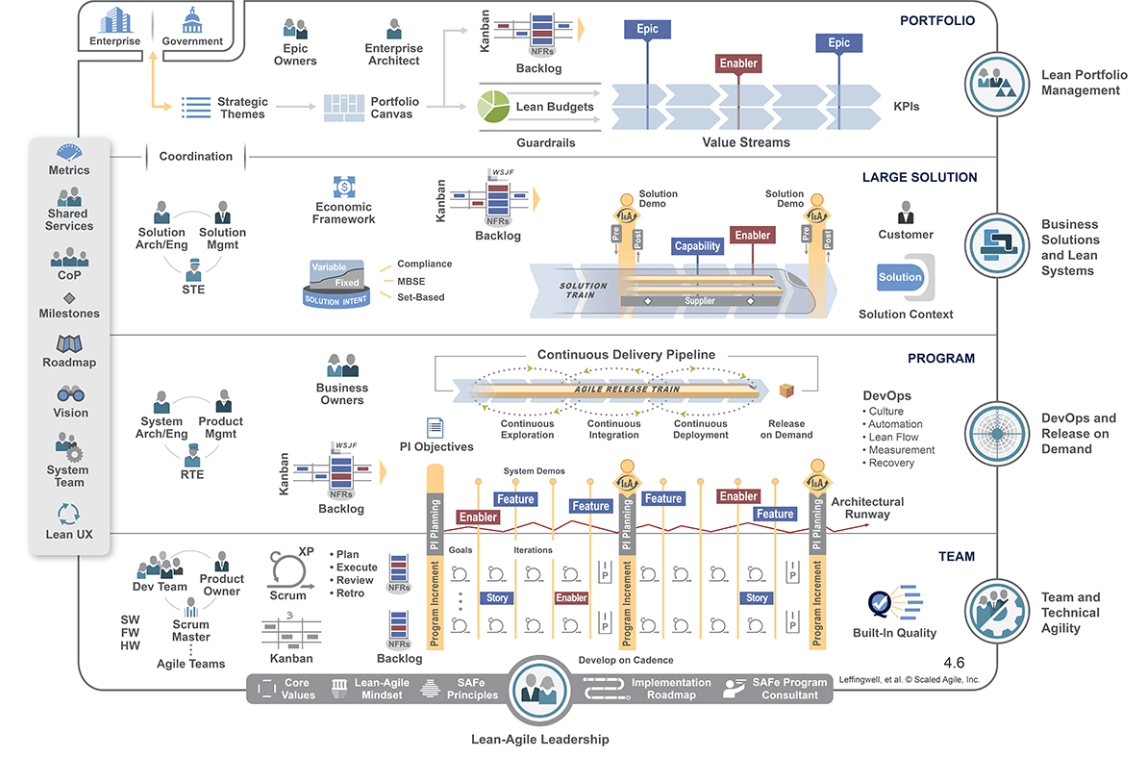
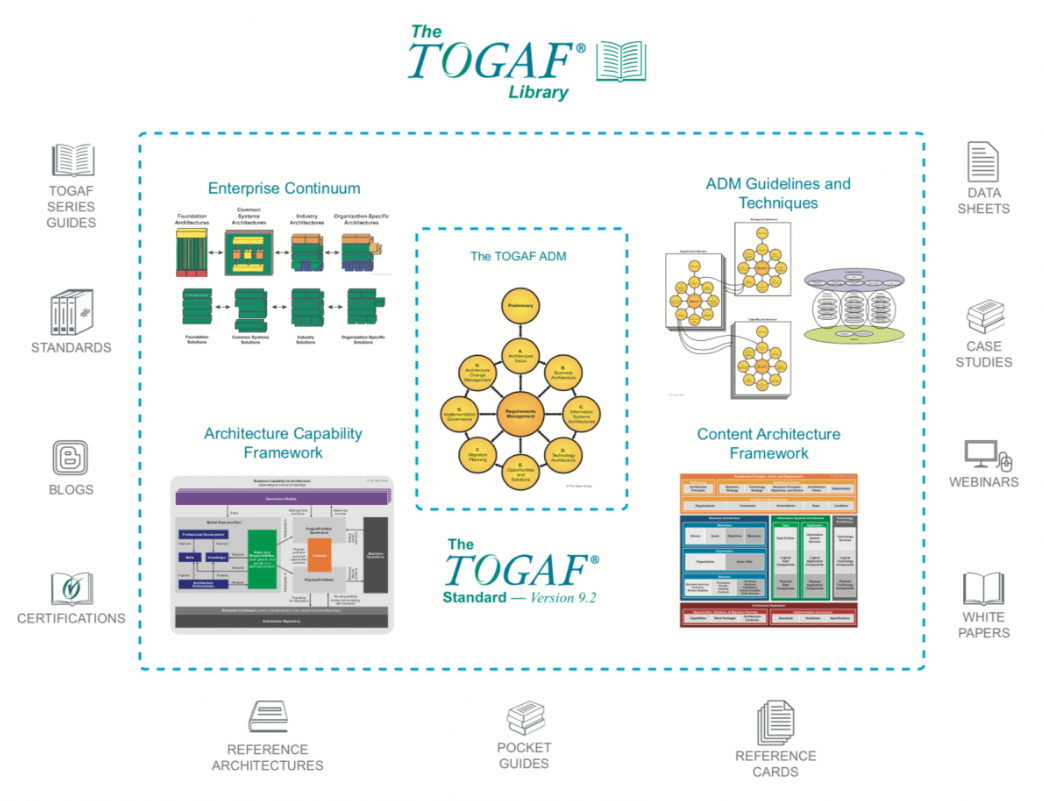
This is the Scaled Agile Framework (SAFe): And this is the top slice of TOGAF. You would use TOGAF as part of the architecture functions in SAFe.
Do you have questions with these steps? Feel free to reach out to me directly: Twitter: twitter.com/musiccomposer1 LinkedIn: www.linkedin.com/in/paulcolmer/ Instagram: www.instagram.com/paulcolmer/ Have an awesome week, beautiful people.
0 Comments
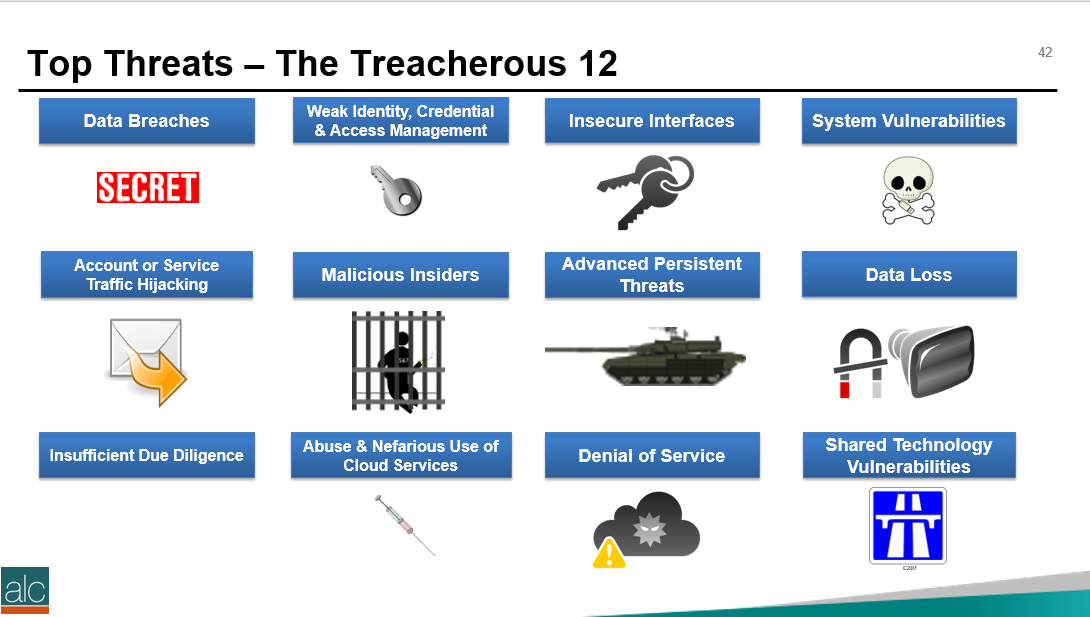
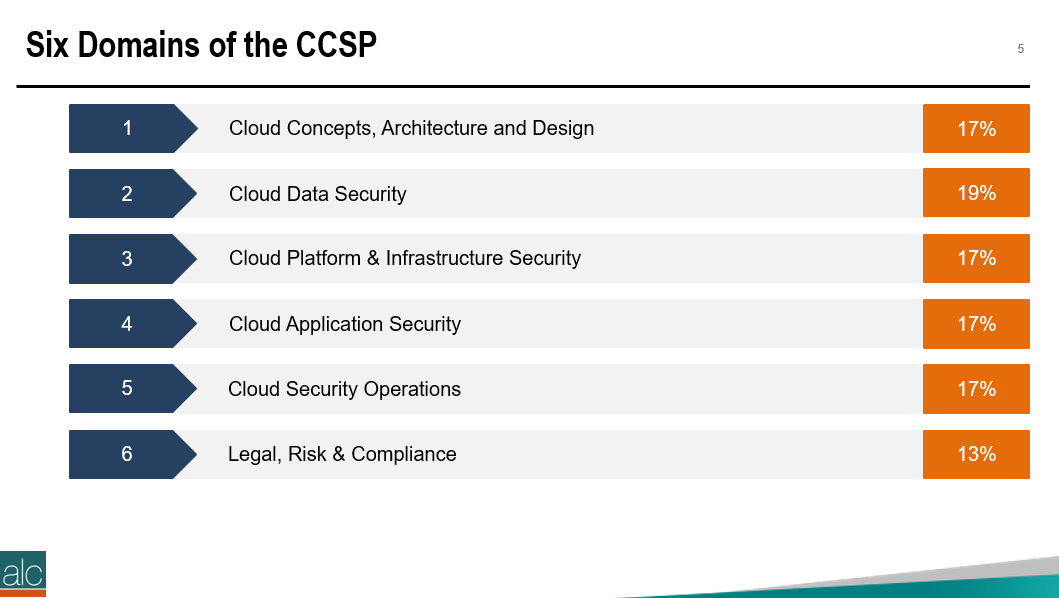
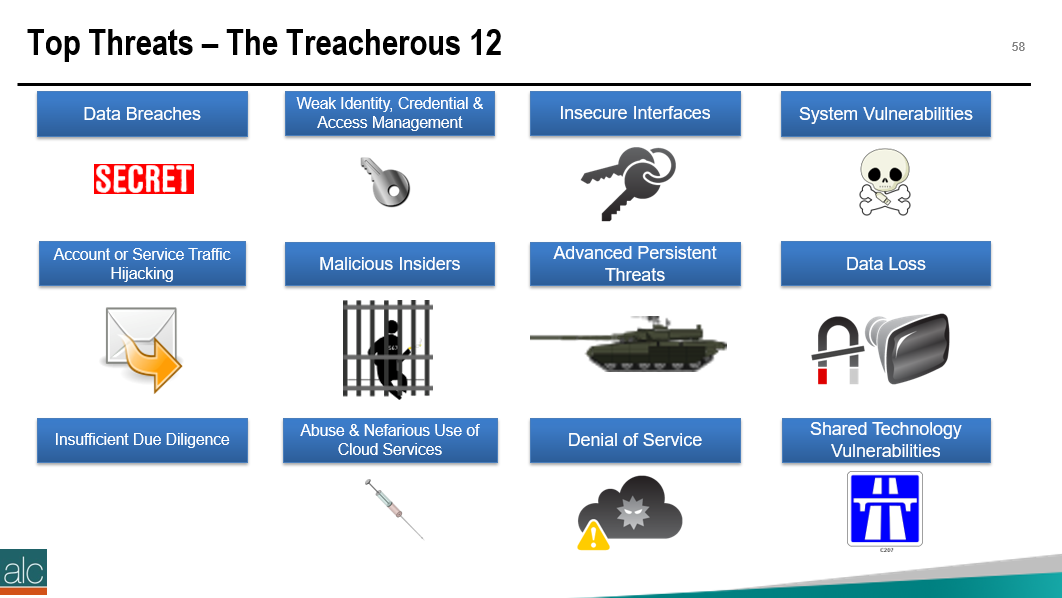
The Certified Cloud Security Professional certification is offered by the ISC2 and is one of the many courses I have helped develop at ALC Training. It is proving to be one of the most popular certifications that I run....I have 11 others that cover cloud computing, agile, cybersecurity and big data areas. But why? As you can see, it covers 6 domains and we focus on a range of techniques and best practices associated with cloud computing. For those studying CCSP, I have created a free flashcard quiz below. This is handy for anyone that is involed in CyberSecurity and is a good way to re-enforce your knowledge. For a detailed list of learning outcomes check out the ISC2 website below.... The reason I think CCSP is popular, is because CyberSecurity is in the Top 5 items that keep senior leaders awake at night. The fear that the organisation you have worked hard to protect, could one day be maliciously attacked is a troubling thought for many...resulting in a cold sweat nightmare at 3am in the morning. To be honest there are many things that business leaders need to consider. So let me outline 2 of the key items that spring to mind this morning.... 1 - Secure the use of Identity and Access Management Systems The key here is people....because they are the solution....not the problem. Here is a simple checklist that everyone can follow...not just at work...but also at home. Tip 05 can be adapted for business, by building a list of trusted sources, i.e. a whitelist. You can do this manually, or by using a whitelisting tool, preferably one based on Artificial Intelligence technology. That way it can detect not just trustued sources that you list, but predict or warn when something looks malicious. 2 - Simulate Probable Security Scenarios Again the key here is people. Create a realistic scenario....data breaches are the most common, so this is a good place to start. Brief a small number of individuals, including leadership, that you're creating a simulated security challenge....execute the scenario for real on a non-production system with the team....then treat it like a fire drill and allow the remainder of the team to see how they react and recover from the simulation. It's a bit like paintballing...where one team attacks the castle....and the other team defends it. Although in this scenario....the defending team is really ascertaining what happened and how best to protect the organisation going forward. If you need inspiration for what threats you should be simulating....take a look at the Treacherous 12....which we cover in the CCSP course. Have a secure and safe day beautiful people. ❤😎🚀
This blog article is designed to be ready by everyone. By everyone, I mean people who are new to the cloud, and maybe uploading a picture of their great grand children to Facebook, for the first time. Or maybe you're a seasoned technologist, like myself, with over 300 cloud-based logins. Chances are, you're probably somewhere in the middle, and this is perfect for you too. The 5 simple tips I have outlined above, will help everyone. They're universal to everyone that uses the cloud. They are simple to implement, and need you to put aside a little time. They will protect you from cyber attacks. Oh...and I also follow these 5 tips myself. Probably for about the past 5 years. I will not only explain how to implement each tip, but I will give you a specific personal examples. That way, you know my advice is real and that I follow my own advice. Only a fake person wouldn't follow their own security advice....right.....? Each image in this blog is clickable, offering additional information about that subject. What is a Complex Password?Let me show you what a complex password looks like: If you click on the image, it will take you to Troy Hunt's blog on passwords and hacking, which explains a bit more around why complex passowrds are important. Let me break this down for you.
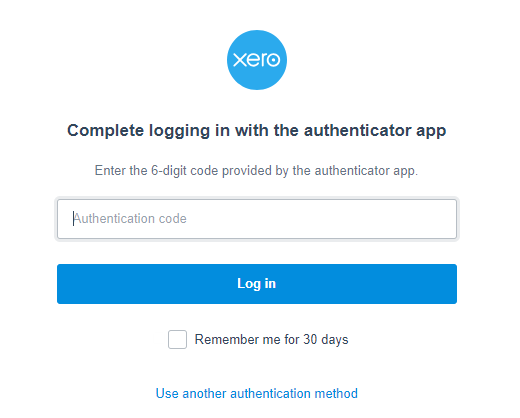
What is Multi-Factor Authentication?It's a service, that most well-known cloud providers, now offer, as a means of additional security protection. Let me break it down with a specific example. I'm going to outline the overall approach using a cloud app called Xero. It is used for accounting and I love it: Using Xero as an example, here is how it works, once it is configured:
If you're not sure, whether you cloud service offers MFA, either contact them directly, or perform a Google search to look up whether they offer the service. You may need someone technical to help setup for you, or if you have paid support, you call up your cloud provider. You can also reach out to me publicly on twitter: @MusicComposer1 I'm always willing to help 'coach' you through to success. What is a Password Manager?t's an app that you download that stores all your passwords for you. It's very, very important that you create a complex password to open the app, as this becomes your key to all your other passwords. You also want to setup multi-factor authentication. Typically the average technical person probably has around 200-500 cloud accounts they use or have used. So for the average person, 50-100 cloud accounts is not unusual. If you're using an app on your mobile phone, then you most likely have a username and password for that app. Therefore if you have 100 Apps on your phone, you will probably have close to 100 usernames and passwords. Clearly it's very difficult to remember 100 different passwords, so the password manager really comes into play here for everyone. There are also two extra benefits, among many, that password managers provide:
When changing your password, I would recommend doing this every 12-24 months, for all your accounts. And also delete cloud accounts that you no longer use. WHY? Because that cloud provider may suffer a data breach in the future. A data breach is where a hacker gains data from a cloud provide. This could mean a malicious actor, could use your account to attempt to steal your money, damage your reputation or worse still assume your identity. My top pick is Last Pass and I would recommend the Premium (Paid) version: What is Anti-Malware Software? This is an app that helps detect any malicious activity on your device. Sometimes known as anti-virus software, however devices can be attacked not just via virus, but also via many other attack vectors. So I prefer the term anti-malware. I personally install anti-malware software on my Android phone and my Windows 10 machine. I don't install it on my Mac or my iPad. However, I would recommend that you install it on all your devices. Generally when you buy anti-malware software they give you a number of licences to run on different types of device, so it probably won't cost you extra. So I always recommend this extra level of protection. The reason I don't do that, is because I have additional security controls to mitigate this risk. These are a little complex to explain. I also don't want to give away this information to potential hackers, who could also exploit me personally. I hope that makes sense. :-) My top pick here is to use the Kaspersky. I've personally used it for probably 10 years now. I came across it, when I was running high-powered flight simulation sofwtare on my machine and I wanted anti-malware software that would detect incoming threats, as well as viruses, without sucking all the processing power from my computer. I found that Kaspersky was the most cost effective and smallest footprint softoware on the market at the time, and have used it ever since. What is SpearPhising or Phising?Never click on links in an email, that are sent from outside your company. WHY? Because you are opening yourself up to a Spearphising attack. Sometimes also known as a Phising attack for short. So a Phising attack, is when a malicious actor, sends you an email with a link inside. You click on the link and a number of bad things can happen:
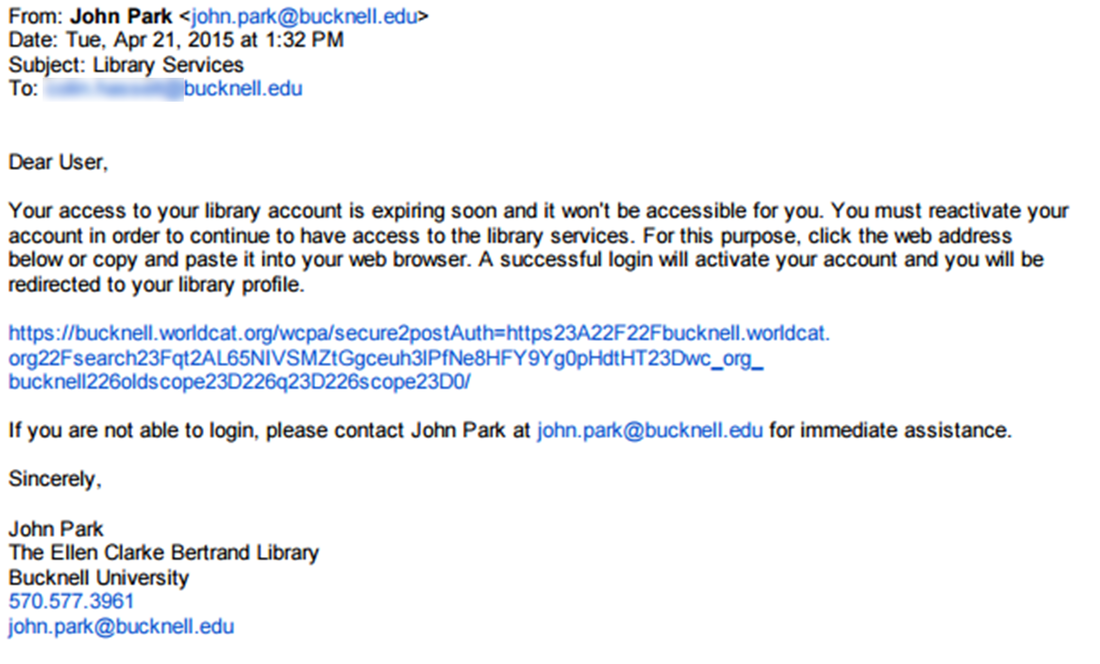
Here is an example, of a reasonably sophicated phising attack: Click on the link above to be redirected to another simple definition of Phising.
But what about if you do business with external companies? That's fine, we can modify this advice. Make a note of all the people you personally deal with outside your company. Agree with them, using the phone, how you're going to communicate via email and how you're going to share information. I personally use the OneDrive cloud links to share read-only files and I always set the link to expire after 30 days. By creating a list, you're effectively creating a 'whitelist'. A list of people whom you trust. There is no guarantee, that someone else won't impersonate them, so by having an agreed format for the exchange, you can validate if it is genuinely from that person. If in doubt, give them a telephone call. You know that old-fashioned thing, that emails has replaced.......LOL. If you're dealing with clients directly via email, then you'll hopefully be validating them as leads anyway, so there shouldn't be any reason to click on the links they are sending you. If you're business is truly an exception to this rule, and clients need to send you a link then you're need additional security:
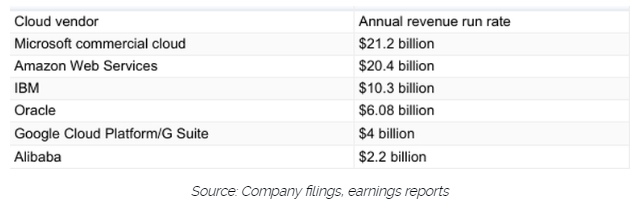
And remember...be aware but not alarmed. Cybercrime is relatively rare. Follow these tips and you'll put yourself in the Top 10% of the population, which means you're highly unlikely to be scammed. Below is a great website to check for the latest scams too: For the first time in 2018, it's become easier than ever to gauge the state of the cloud market. New data from the top cloud providers, mean we can really see who is dominating the landscape. In this blog, I've chosen to look at the total revenue as an indicator of success. Partly because it's easy to measure, but also because it given an indication of relative market opportunity and growth. This chart is taken from a great ZDNET article that was published earlier this year: www.zdnet.com/article/cloud-providers-ranking-2018-how-aws-microsoft-google-cloud-platform-ibm-cloud-oracle-alibaba-stack/ It clearly shows Microsoft as the dominant force, which I predicted would be the case back in 2016. My colleagues at DXC Technology will attest to that prediction. I think it's also a reflection on a number of compelling events that have materialised over the past few years:
On the Amazon Web Services side, there is much progress and improvement especially in the area of new services. AWS are very good in the Serverless and PaaS spaces, adding a whole series of new innovations. These and exciting innovations were announced at the AWS ReInvent 2017 conference last year and include:
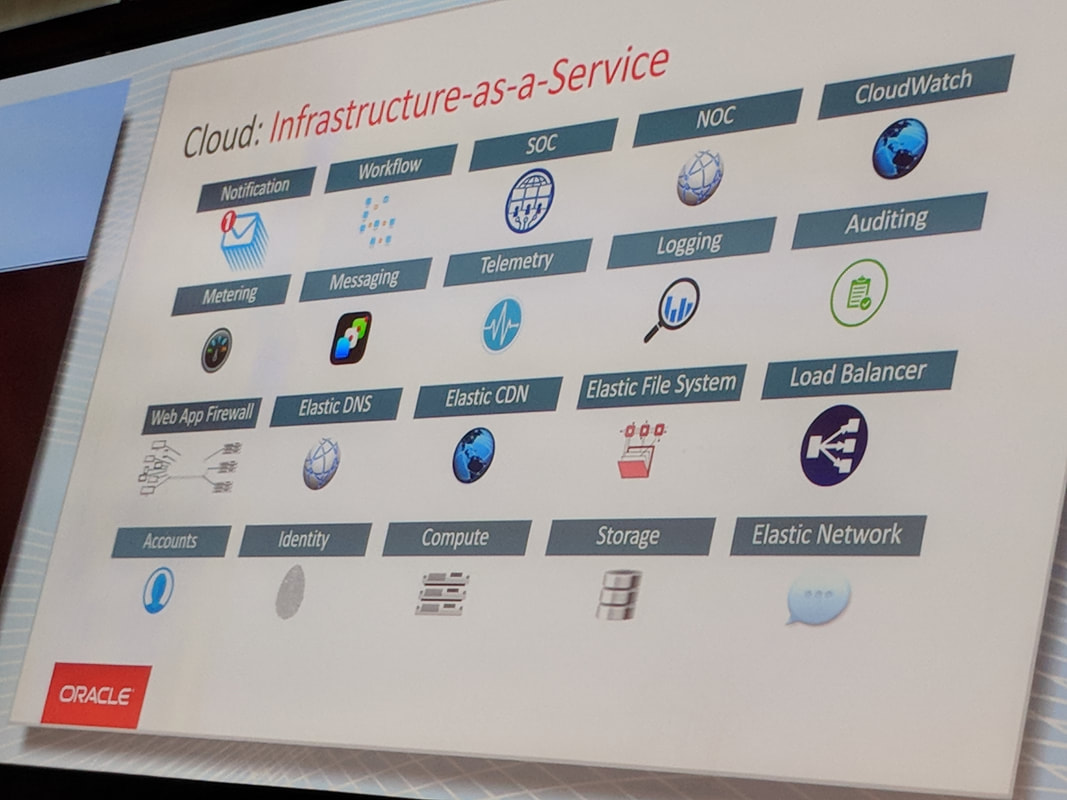
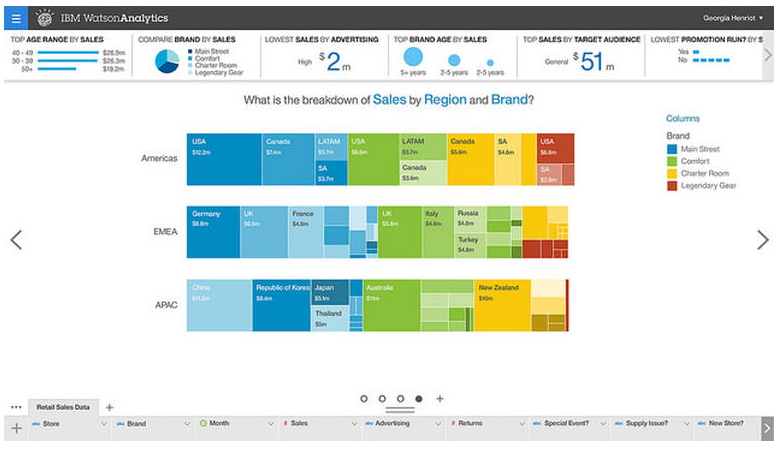
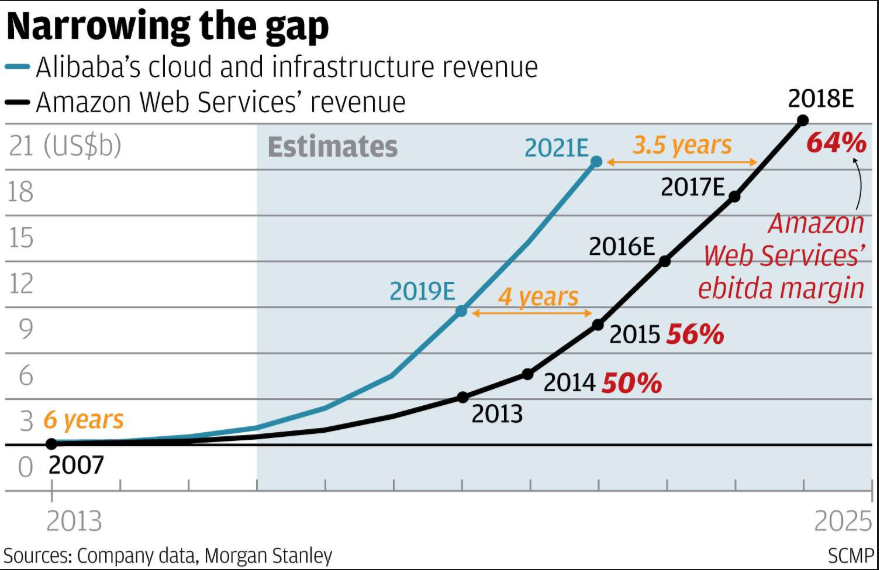
Oracle are coming up fast, probably as a result of their push in the past 12-18 months. A rep at Oracle invited me to attend Oracle Cloud World, which introduced me to the maturity and sleek look of their latest cloud offerings. The pics below gives a quick overview of the Oracle Cloud offerings: IBM is a little way behind the Top 2 leaders with their suite of cloud offerings. IBM Watson is probably the best known. I'm still waiting for IBM to approach me to, and invite me to their conference. Check out the screenshot below: More information on IBM cloud services can be found here: www.ibm.com/services/cloud?lnk=hpmse_ts&lnk2=learn Alibaba are a definitely one to watch. My prediction, is that by 2020 Alibaba will be No. 3 by revenue and may well be looking to eat up AWS with a takeover strategy, to compete with Microsoft. Here is a quick overview of the predicted growth of Alibaba revenue vs AWS: And here is a good article that articulates how large and dangerous Alibaba really is. I do apologise for all the popups, but the free content on the site IS worth the pain: www.cbinsights.com/research/amazon-alibaba-international-expansion/ The link below gives another perspective on the Microsoft / AWS revenue growth story, outlining some of the great customers stories to come out of the Azure platform. These include:
Finally if you feel you need some specialised training or business advice on AWS, Microsoft Azure, IBM, Oracle or Cloud CyberSecurity, feel free to reach out to me or to ALC Training: www.alctraining.com.au/courses/cloud-computing/ #CloudComputing #Cloud #AWS #Amazon #Microsoft #Azure #Office365 #CyberSecurity #CCSP #Training #Coaching #AI
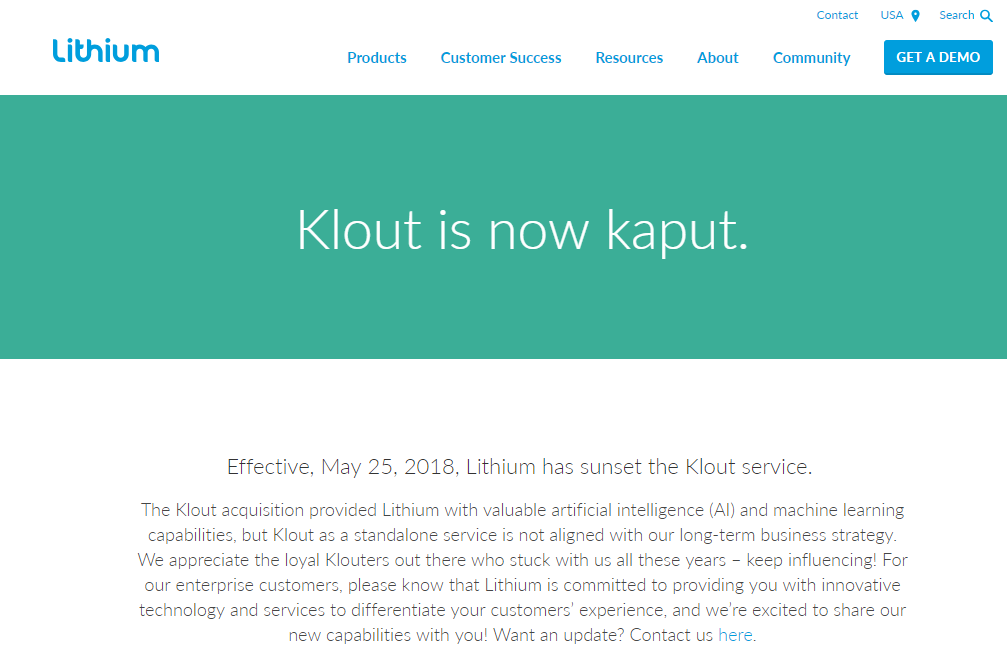
Klout was a social media tool that helped online influencers measure their influence in the virtual world. It was bought for $200 million by a company called Lithium in 2014. It targeted the most popular social media platforms such as twitter, instagram, linkedin and youtube and provided you with an influencer score. The higher the score, the more influential you were likely to be. As of the 25th of May, Klout was retired. This co-incided with the timing of the new European Union, General Data Protection Regulation (GDPR) laws. These came into force on the same date. So why did Lithium retire Klout? It really boils down to return on investment. Lithium bought the people, intellectual property and the technology, to help them inprove their products. They specialise in creating products that improve your business customer service, via social media channels. Understanding the influence and pervasiveness of a brand, was crucial to their strategy, and Klout provided this service. This allowed Lithium to acquire talent and knowledge. In addition, Klout does not provide an obvious or known revenue stream for Lithium, as it's a free tool. It's a similar problem that Facebook and Twitter had faced in the past, until they utilised advertising and promotion as a means of making revenues. Finally GDPR is complex legislation with a heap of complexities associated with it. Let's provide some real examples using Klout: Klout is used by millions of social media users around the world. A proportion of them live in the EU, which consists of 28 separate countries. That means Lithium would need to comply with the GDPR legisation. This would include some key investments in the Lithum business to comply with GDPR. Here are some examples:
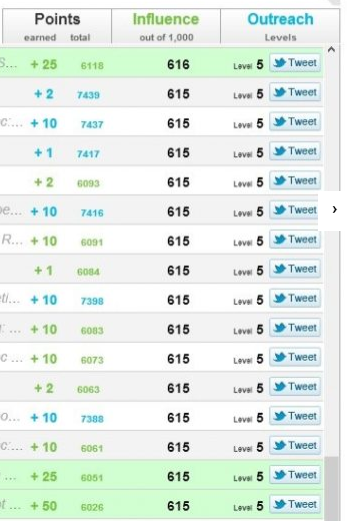
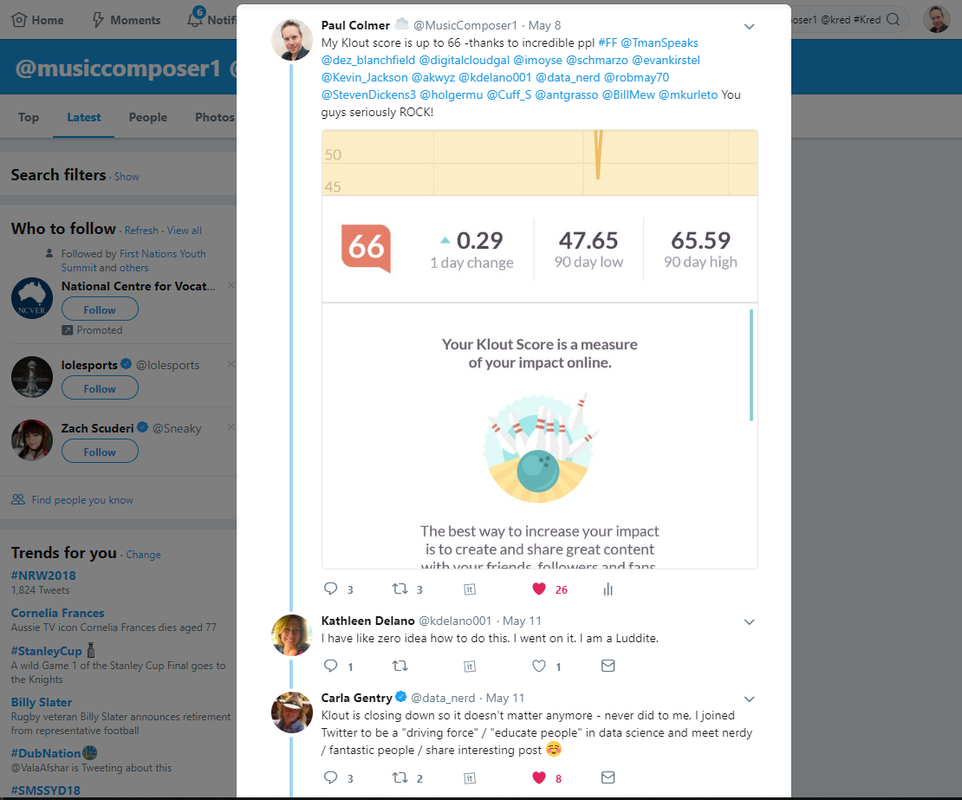
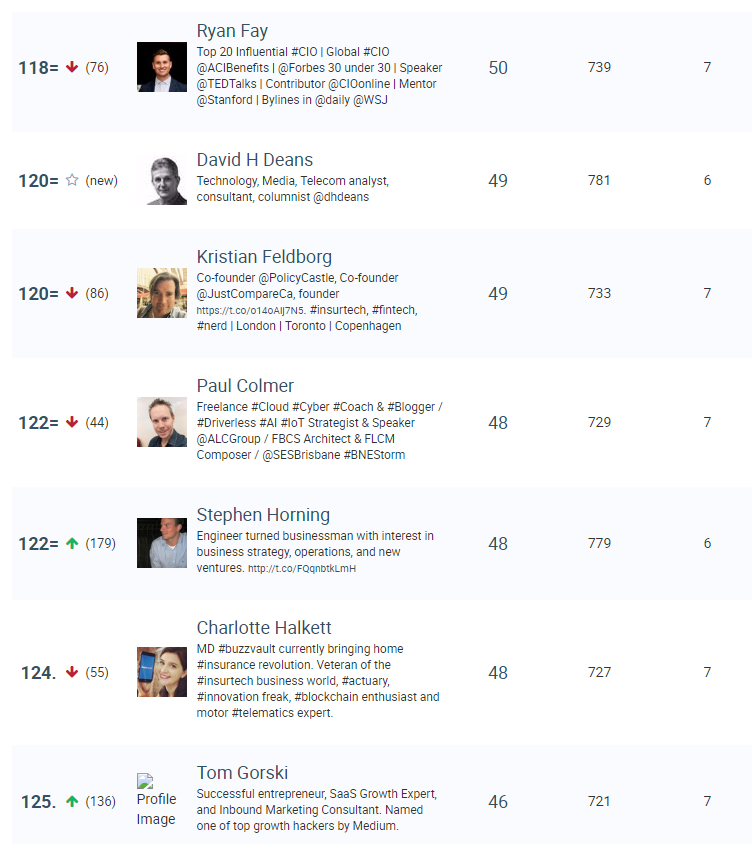
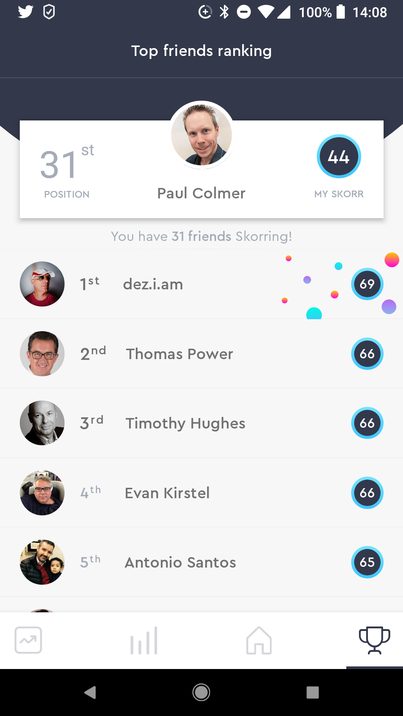
https://www.alctraining.com.au/blog/what-is-gdpr/ The great news for social media influencers, like myself, is that there are 2 viable alternatives to Klout: Kred www.go.kred/?_ga=2.230454108.133662099.1527544788-1662686162.1527021072 Skorr www.skorr.social/ Kred appears to be better known and scores both influence and outreach using a publicly available algorithm. "Influence" measures the likelihood that someone will act upon the user's posts, and "Outreach" measures the user's tendency to share other people's content. Independent information around Kred is available here: https://en.wikipedia.org/wiki/Kred_Influence_Measurement The way in which Kred scores a user can be seen the following screenshot which shows how it allocates the metrics for influence and outreach. This information is available when the user logs in and provides an audit trail of how the scores have been calculated: Unfortunately I've not been able to log in to my Kred account. I wanted to check that these audit records are being created and validate that it provides transparency. I'm simply greeted with an OAUTH error every time I attempt to use my Twitter or LinkedIn accounts. No response to emails but a very positive response via Twitter outlining to me and my fellow influencers, that they'll fix it in their new Kred 2.0 version to be released on 11 June 2018. Many of the influencers in the chat had similar error to myself. You can get check out the live chat here: twitter.com/MusicComposer1/status/993675262050033670 Another upside to Kred, is that there is open API integration into the platform. Which means third pary companies that wish to use the data, can do so. Here is a great example of how Kred is being used by Rise.Global to create social influencer charts. Unfortunately for me, my ranking was better with Klout than Kred: Skorr although not as well known, really impressed me with the downloable Android app, that is a work of art in itself. Very easy to use. No problems with OAUTH or login and a few really awesome features in the app. My favourite is the chart which shows where you are in terms of score in relation to your fellow influencers. As you can see I have some catching up to do.... It also includes a really great FAQ that answers many of my questions, around how the app scores you. You can see the FAQ here: skorr.social/newsroom/media-info/SKORR-FAQ_v0051.pdf The only downside, seems to be from a developer perspective, as the APIs are not available for general use. This means it can't be used by 3rd parties. You could argue that is a good thing, if you don't want your score to be used autonomously in an app. Or a bad thing, if you want to see how you rate against other influencers in a 3rd party charting system. Overall I believe in open APIs, so I see this as a downside for the world of influencing.
Interesting in learning more about social media scoring, GDPR or cloud security, please feel free to check out my portfolio of cloud training courses at ALC Training: www.alctraining.com.au/courses/cloud-computing/ |
CategoriesAll Active Directory AI Architecture Big Data Blockchain Cloud Comedy Cyber DevOps Driverless Cars MicroServices Office 365 Scaled Agile Social Media AuthorPaul Colmer is an AWS Senior Technical Trainer. Paul has an infectious passion for inspring others to learn and to applying disruptive thinking in an engaging and positive way. Archives
May 2023
|
















 RSS Feed
RSS Feed