|
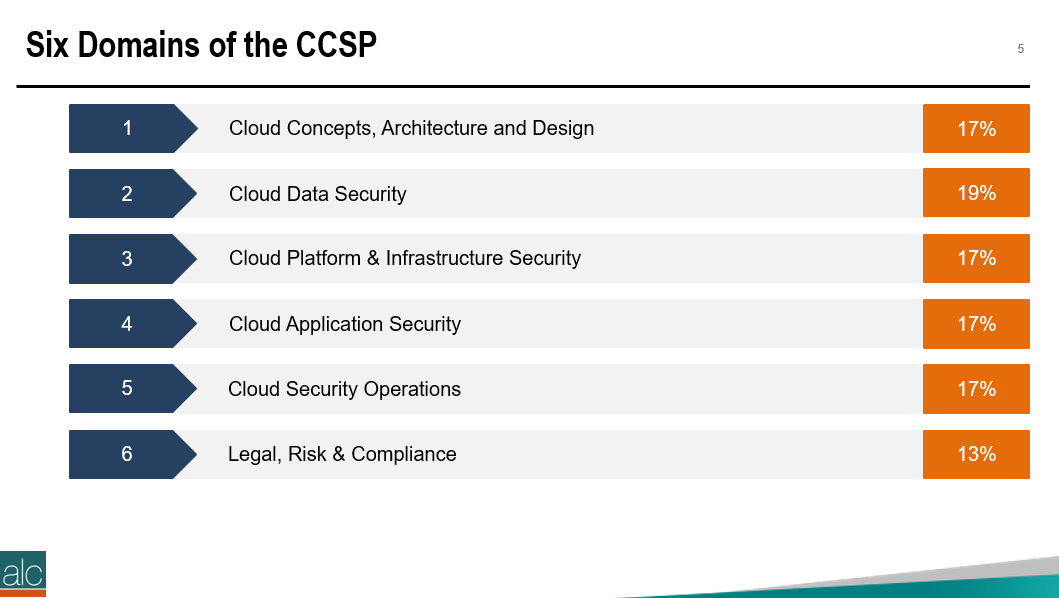
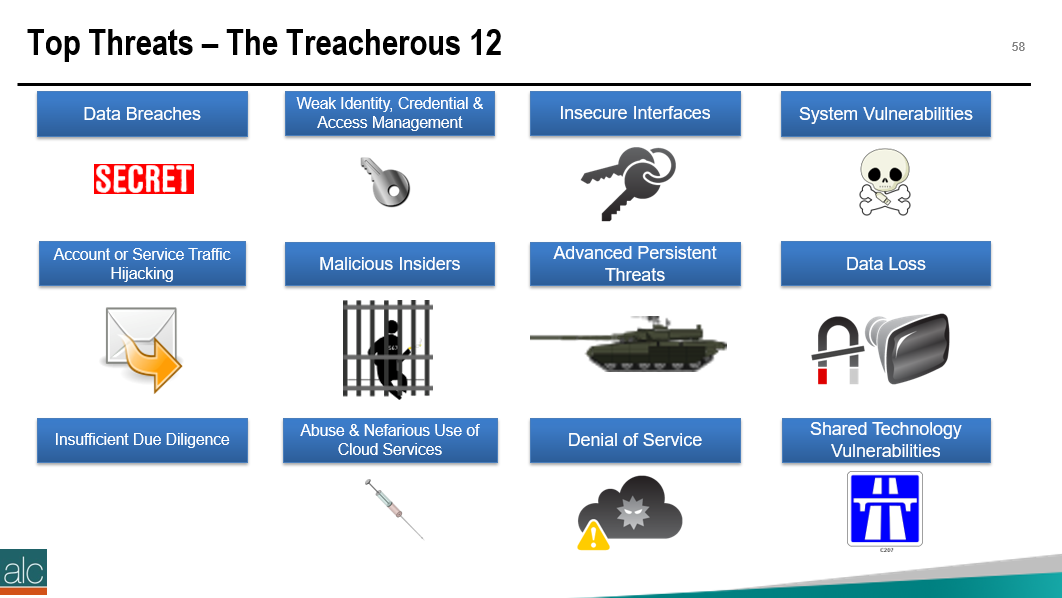
The Certified Cloud Security Professional certification is offered by the ISC2 and is one of the many courses I have helped develop at ALC Training. It is proving to be one of the most popular certifications that I run....I have 11 others that cover cloud computing, agile, cybersecurity and big data areas. But why? As you can see, it covers 6 domains and we focus on a range of techniques and best practices associated with cloud computing. For those studying CCSP, I have created a free flashcard quiz below. This is handy for anyone that is involed in CyberSecurity and is a good way to re-enforce your knowledge. For a detailed list of learning outcomes check out the ISC2 website below.... The reason I think CCSP is popular, is because CyberSecurity is in the Top 5 items that keep senior leaders awake at night. The fear that the organisation you have worked hard to protect, could one day be maliciously attacked is a troubling thought for many...resulting in a cold sweat nightmare at 3am in the morning. To be honest there are many things that business leaders need to consider. So let me outline 2 of the key items that spring to mind this morning.... 1 - Secure the use of Identity and Access Management Systems The key here is people....because they are the solution....not the problem. Here is a simple checklist that everyone can follow...not just at work...but also at home. Tip 05 can be adapted for business, by building a list of trusted sources, i.e. a whitelist. You can do this manually, or by using a whitelisting tool, preferably one based on Artificial Intelligence technology. That way it can detect not just trustued sources that you list, but predict or warn when something looks malicious. 2 - Simulate Probable Security Scenarios Again the key here is people. Create a realistic scenario....data breaches are the most common, so this is a good place to start. Brief a small number of individuals, including leadership, that you're creating a simulated security challenge....execute the scenario for real on a non-production system with the team....then treat it like a fire drill and allow the remainder of the team to see how they react and recover from the simulation. It's a bit like paintballing...where one team attacks the castle....and the other team defends it. Although in this scenario....the defending team is really ascertaining what happened and how best to protect the organisation going forward. If you need inspiration for what threats you should be simulating....take a look at the Treacherous 12....which we cover in the CCSP course. Have a secure and safe day beautiful people. ❤😎🚀
https://twitter.com/DigitalColmer
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
CategoriesAll Active Directory AI Architecture Big Data Blockchain Cloud Comedy Cyber DevOps Driverless Cars MicroServices Office 365 Scaled Agile Social Media AuthorPaul Colmer is an AWS Senior Technical Trainer. Paul has an infectious passion for inspring others to learn and to applying disruptive thinking in an engaging and positive way. Archives
May 2023
|





 RSS Feed
RSS Feed