|
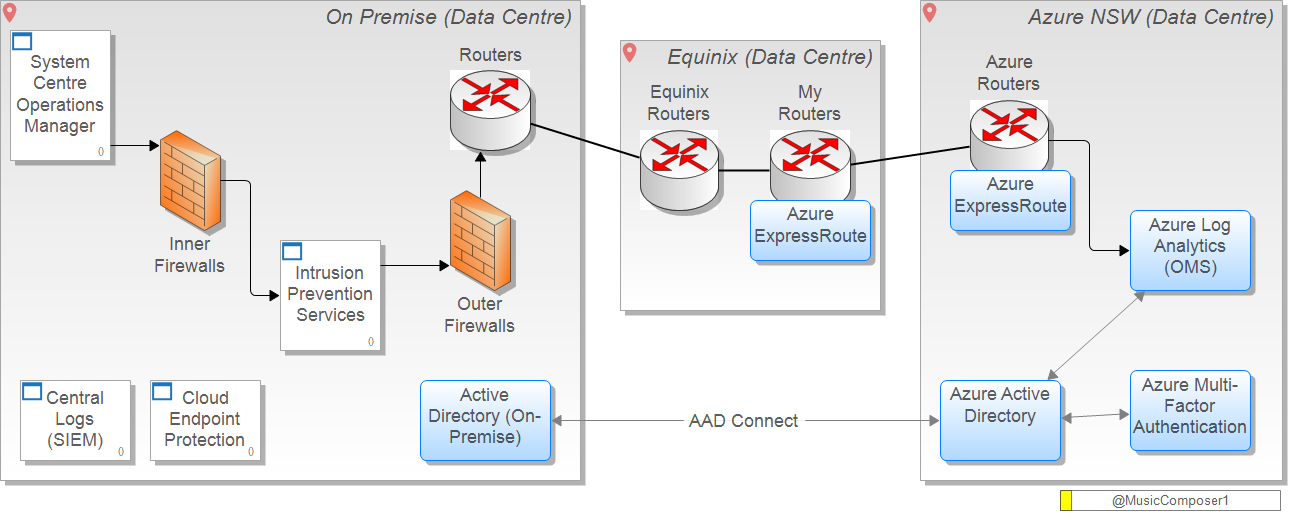
I had a fantastic question come through to me via twitter from a research student. He is doing a research thesis on access control mechanisms and wanted to know under what circumstances Microsoft Identity Manager (MIM) should be used over Azure Active Directory (AAD) connect. Firstly let's establish Azure Active Directory (AAD) is used for: https://docs.microsoft.com/en-us/azure/active-directory/connect/active-directory-aadconnectsync-whatis In a nutshell it allow you to create federated and synchronised contact information between one or many active directory domains with one or many Azure active directory domains. Here is an example of where you could use federation using AAD Connect. This is part of a wider architecture that allows you to integrate your SCOM monitoring data with Azure Log Analytics in OMS, using multi-factor authentication: The predecessor to Microsoft Identity Manager is Forefront Identity Manager, known as FIM, and with mainstream support ending in October this year and end of life expected in 2022: https://blogs.technet.microsoft.com/iamsupport/2017/02/22/warning-forefront-identity-manager-fim-mainstream-support-is-ending-10102017/ MIM has all the features of FIM plus a few more. Here is a great overview of MIM, which builds on the existing FIM features: https://docs.microsoft.com/en-us/microsoft-identity-manager/microsoft-identity-manager-2016 From my own experiences with FIM, MIM and AAD Connect, my thoughts are that it depends on the specific level of control you need. For example, if you have customised your Active Directory schema heavily and you have apps in your forest that use these customised data items, then you'll likely need more control and flexibility with your on-premise AD to Azure AD data synchronisation settings. Especially if you decide to move or migrate the apps that are utilising the custom meta-data, to the cloud. Another use-case is if you wish to use one of the inbuilt connectors to help federate between internal systems and AD on-premise. FIM comes with 3 connectors for example:
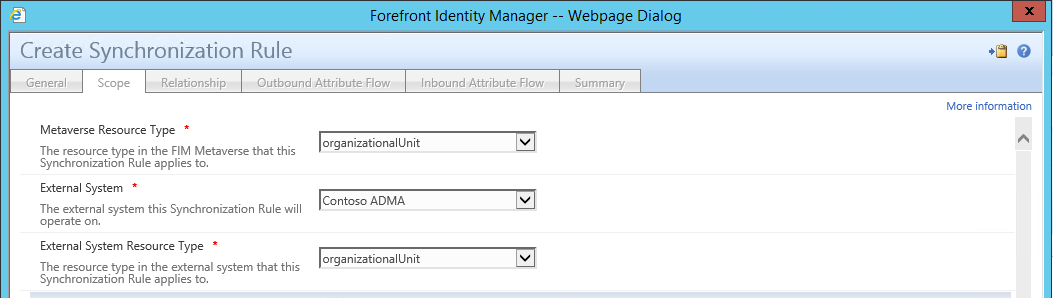
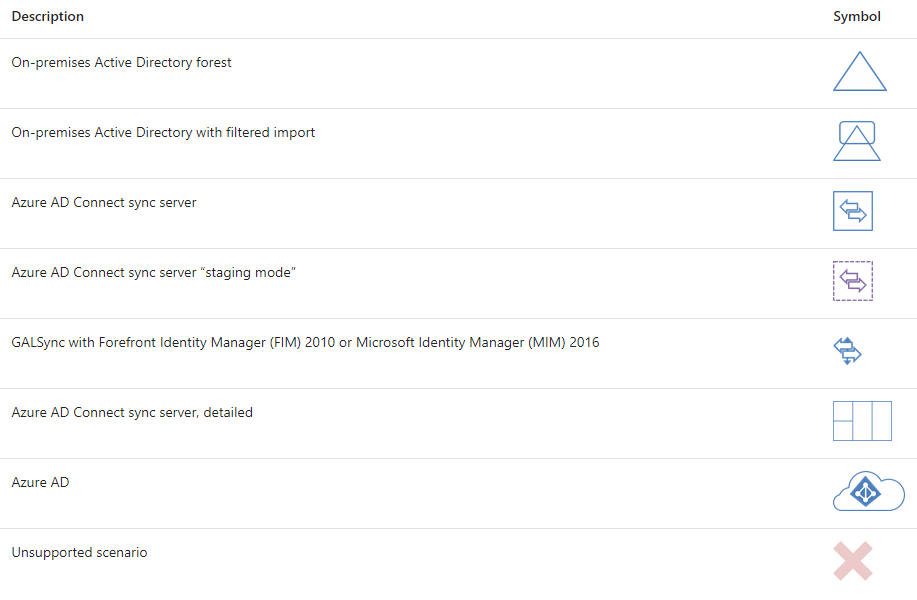
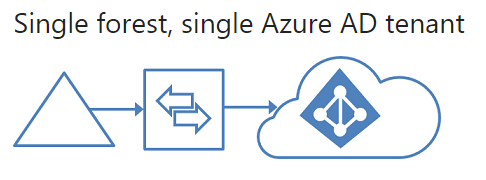
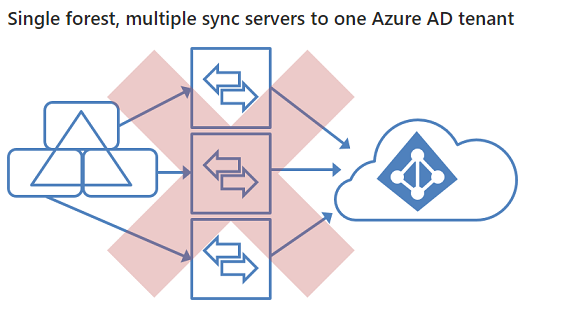
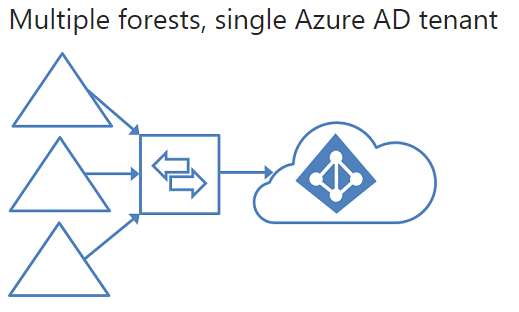
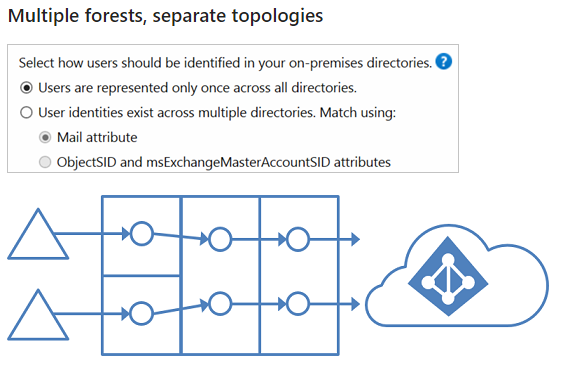
Microsoft Identity Manager does a great job of allowing you set custom synchronisation rules to provide that level of granularity. This article is based on the FIM sync rules, but still applies to MIM: https://blogs.msdn.microsoft.com/connector_space/2014/12/24/introducing-synchronization-rules-part-1/ Unfortunately, AAD Connect is also a moving target with features being constantly released that make it less feasible to use MIM. After a bit of digging around to find out the specific use cases, I found this great article on TechNet: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-hybrid-identity-design-considerations-tools-comparison It clearly outlines all the key features that AAD currently support and that FIM supports. As you can see there are many features that are marked in AAD as 'future release'. But at the time of writing the following features were only supported with MIM: I also found this incredible resource, with outlines very clearly all the architectural patterns that are supported with AAD Connect: https://docs.microsoft.com/en-us/azure/active-directory/connect/active-directory-aadconnect-topologies#staging-server And here are some of the diagrams from the link showing the various patterns. If there is a red X shown it's an unsupported pattern: And there you have it. A very quick summary of resources that will help you decide whether to go AAD Connect or MIM for your organisation.
I always recommend the to start with a test setup of AAD Connect and a copy of your on-premise AD and simply identify several different use-case scenarios that you currently encounter. I think it's most likely that 90% of the time AAD Connect will be enough. The 10% being service providers hosting multiple clients with complex active directory requirements, or companies that have 100's of domains spread across several countries, with connections to internal systems for advanced identity federation. And yes, some clients really do have 100's of domains….. Paul Colmer is the lead digital architect ALC Training and Consulting. He is responsible for creating and running all the cloud security courses, which include CCSP, AWS, Azure, Office 365 and cloud foundation certifications. For more information visit: ttps://www.alctraining.com.au/courses/cloud-computing/ Or engage with Paul on his crazy adventures on twitter: @musiccomposer1 using the hashtag #CCSP https://twitter.com/DigitalColmer
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
CategoriesAll Active Directory AI Architecture Big Data Blockchain Cloud Comedy Cyber DevOps Driverless Cars MicroServices Office 365 Scaled Agile Social Media AuthorPaul Colmer is an AWS Senior Technical Trainer. Paul has an infectious passion for inspring others to learn and to applying disruptive thinking in an engaging and positive way. Archives
May 2023
|


 RSS Feed
RSS Feed